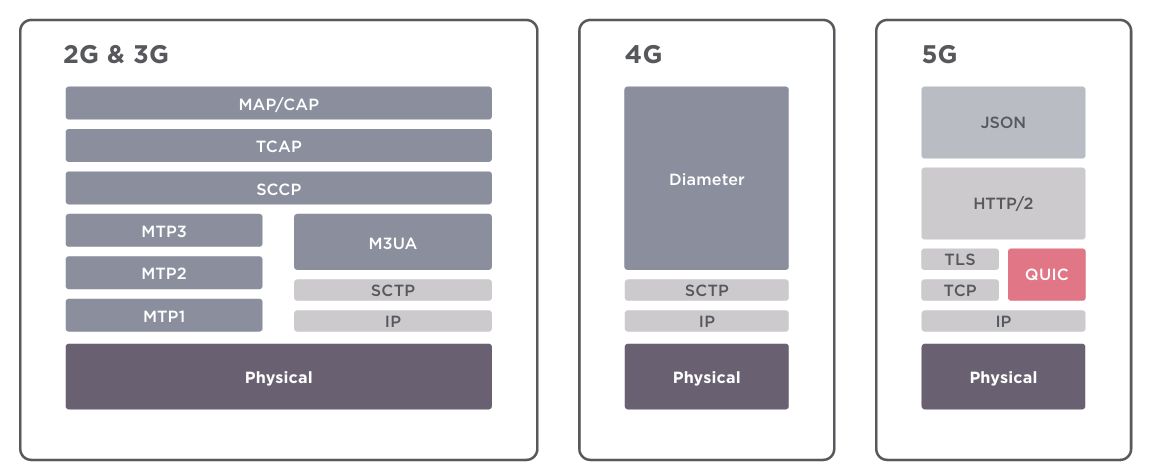
?Previous generations relied on the SS7 and Diameter protocols. The 5G network core is built on well-known Internet protocols such as HTTP and TLS.
? Security threats associated with 3G and 4G will remain after 5G reaches the public and heavily influence NR deployments. However, the main challenge with 5G is that Internet technologies are open and well-known to attackers. There are many techniques for searching for vulnerabilities, and numerous tools are available for easy exploitation.
? Example: In 2018, web attacks accounted for a quarter of all security incidents, and according to GSMA, 67% of web applications contain high-risk vulnerabilities.
? Even with the new 5G Security signalling protocols, Attackers who previously were prevented by complex telecom-specific protocols will target 5G networks built on the technologies they already know how to hack.
?Security is a process, not a one-and-done event. Despite a great deal of 5G security work at the standards level, significant unknowns remain.
