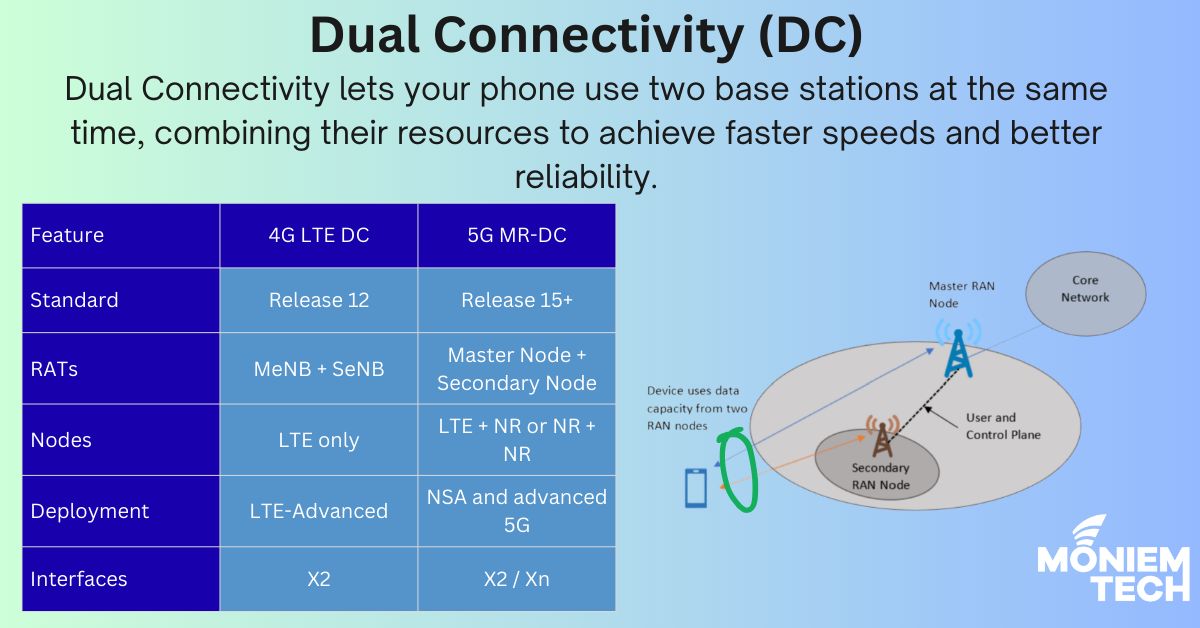
Most people in the industry connect Dual Connectivity (DC) with 5G Non-Standalone (NSA) deployments. However, this view overlooks the long history and key role of DC, which has quietly supported […]
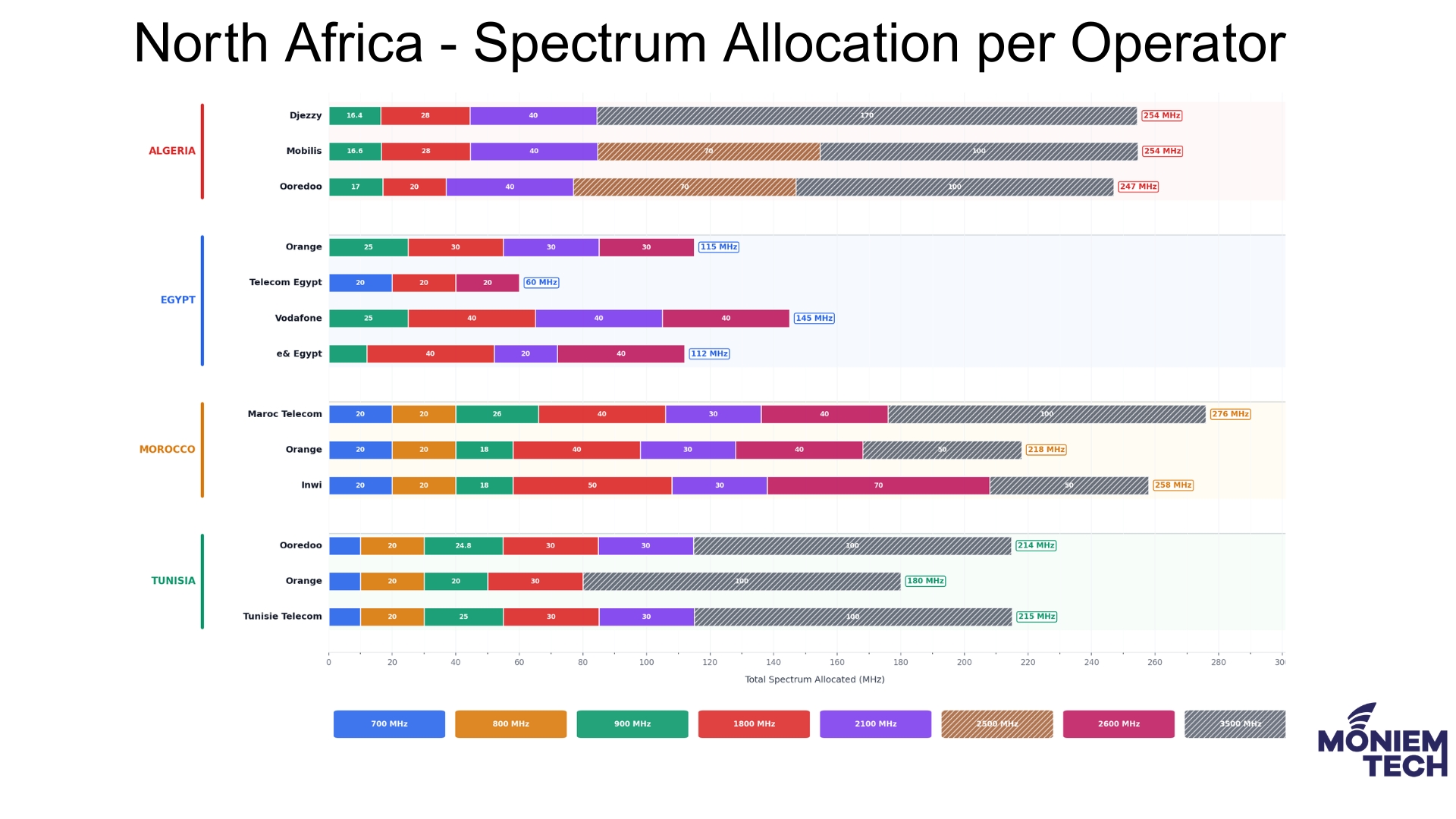
As 2025 became the 5G launch year across North Africa (Tunisia, Egypt, Morocco, Algeria), I took a deeper look at spectrum holdings and allocations — and the story goes well […]
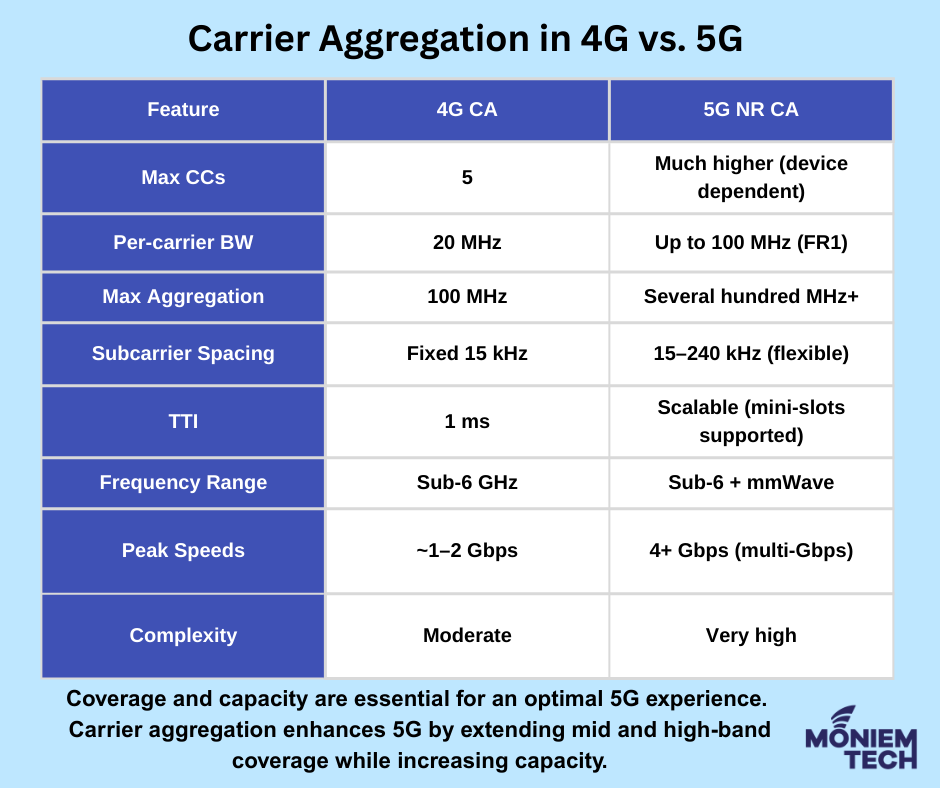
Carrier Aggregation (CA) combines multiple frequency blocks (Component Carriers) into a single larger channel, boosting speed, capacity, and coverage. It’s been around since 4G, but in 5G it’s evolved into […]
Have you ever seen “5G-A” or “5.5G” on your phone? Do you care about the icon… or only the experience you actually feel? That little 5GA logo (like the one […]
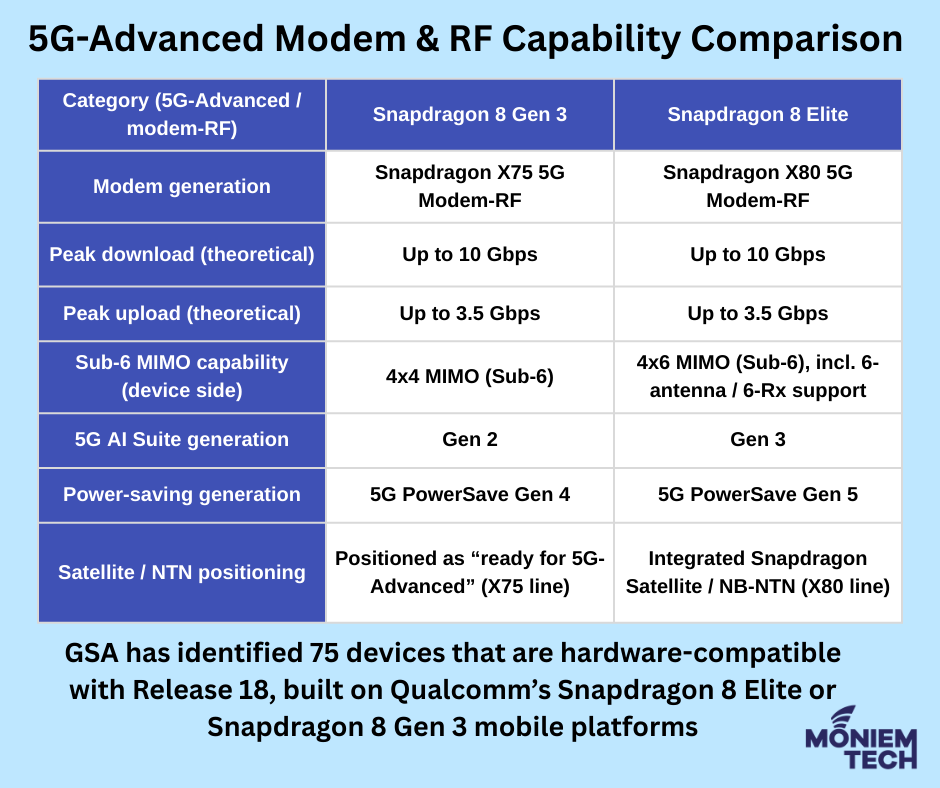
5G-Advanced, standardized in 3GPP Release 18, is now shifting from “spec on paper” to real-world commercial rollouts. While operator deployments and feature roadmaps are accelerating, the device ecosystem remains in […]

In January 2026, India’s Department of Telecommunications (DoT) announced that the lower 6 GHz band (5925–6425 MHz) can be used license-free for Low-Power Indoor (LPI) and Very-Low-Power (VLP) Wi-Fi and […]
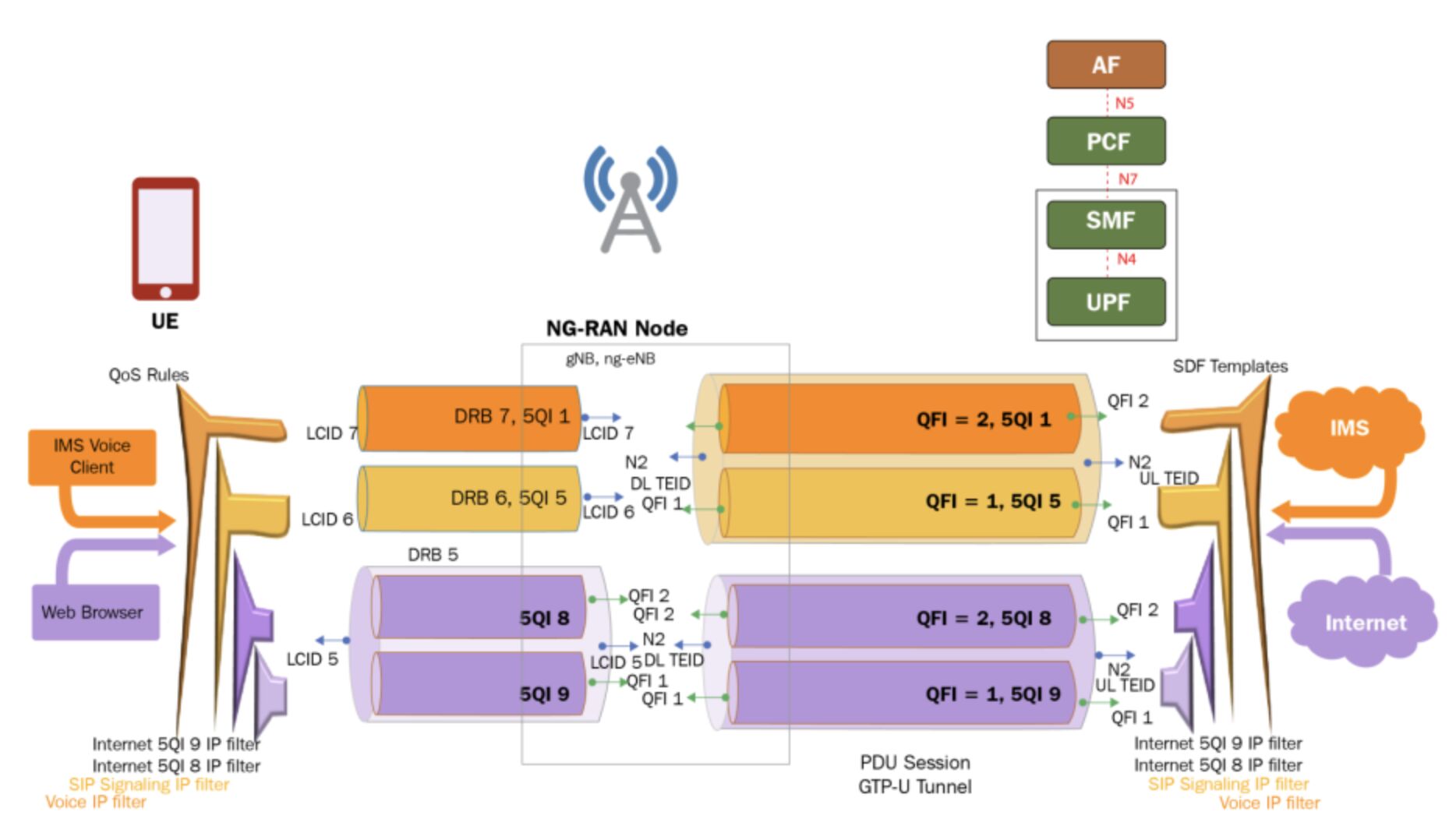
Most people see 5G as higher throughput. However, Engineers see something deeper: the SDAP layer (Service Data Adaptation Protocol) — a new 5G protocol that fundamentally changes how QoS is […]

GSMA has identified a critical need for an average of 2 to 3 GHz of mid-band spectrum per country by 2030, noting the consequences of a shortage of mid-band bandwidth, […]
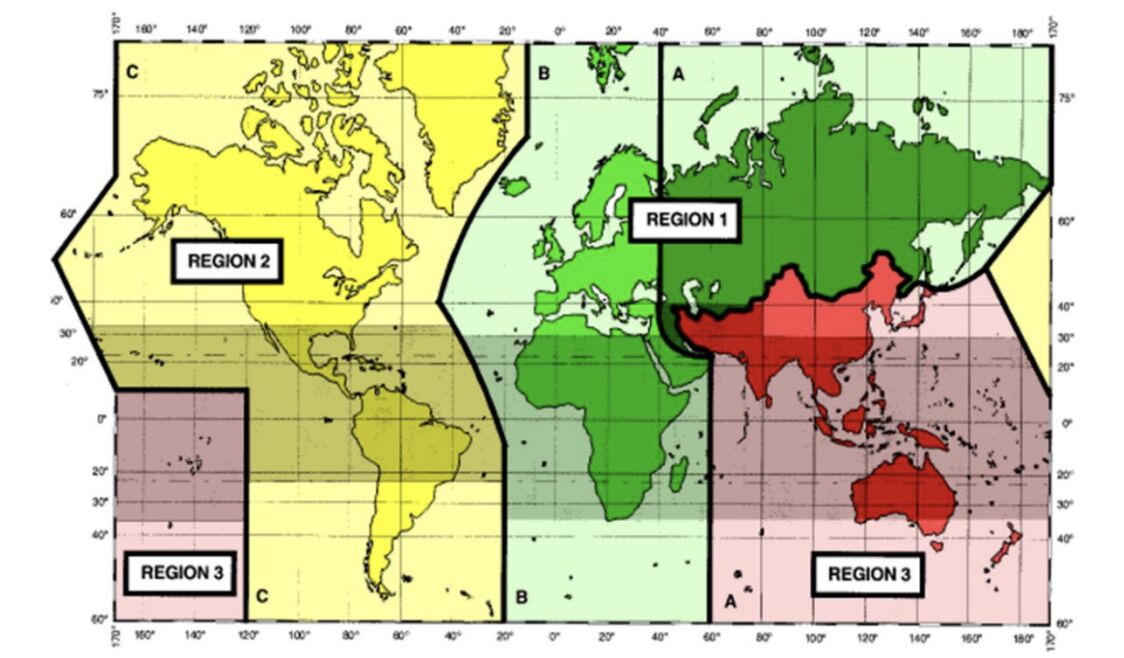
In my first post of 2026, I’d like to share a brief, practical overview of the radio spectrum—the actual blood of connectivity. The ITU Radio Regulations govern global spectrum use […]

When we talk about mobile network performance—coverage, speed, latency—we often focus on spectrum, RAN, or core evolution. Yet, Backhaul remains one of the most critical (and sometimes underestimated) components of […]

Many people ask: “5G NSA or even 5G SA already gives great speed, latency and quality – so why do operators now push 5G-Advanced (3GPP Rel-18) to consumers, not just […]
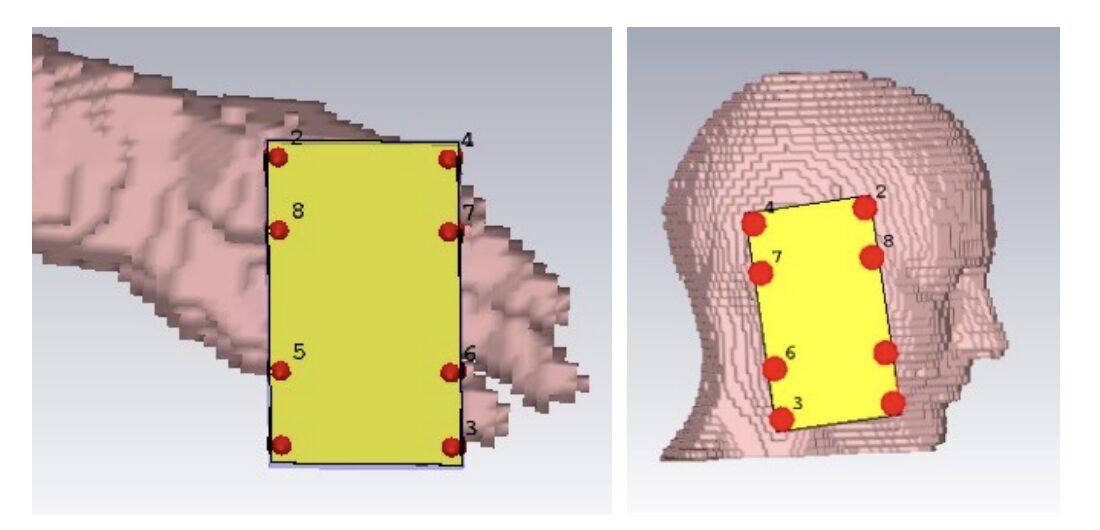
Short answer: No — and here’s why. Imagine buying a new 5G phone only to discover it uses one RF chain. What would that mean for your experience? Would the […]
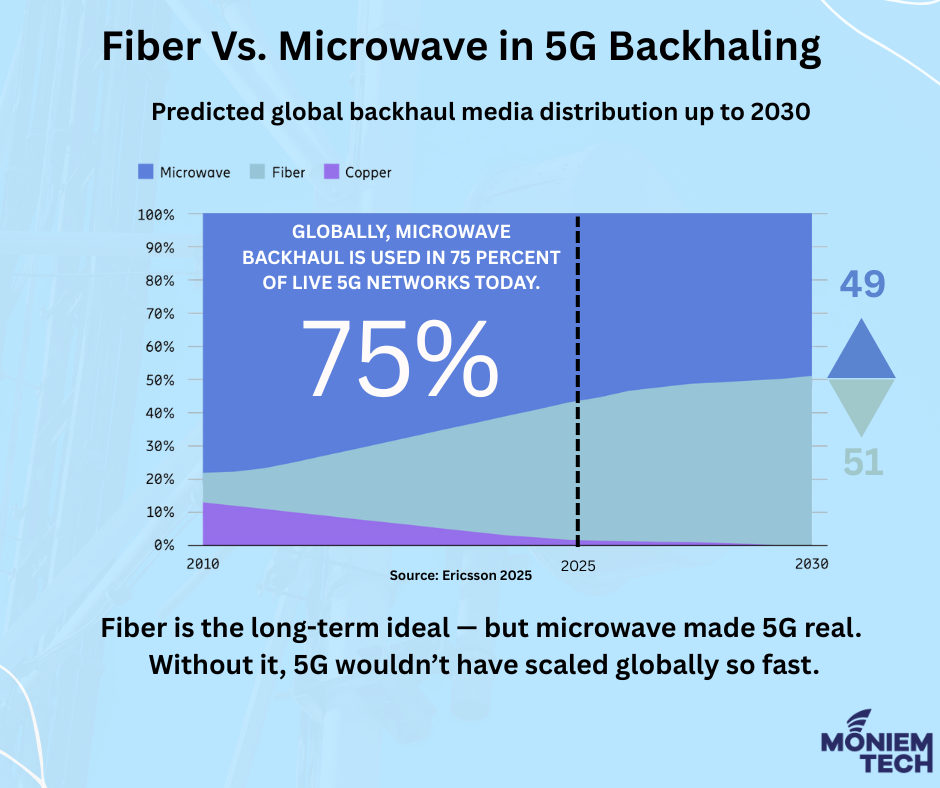
Fiber is the king of capacity — but Microwave is the knight of speed, flexibility, and reach. The choice between fiber and microwave is not about which is “better,” but […]
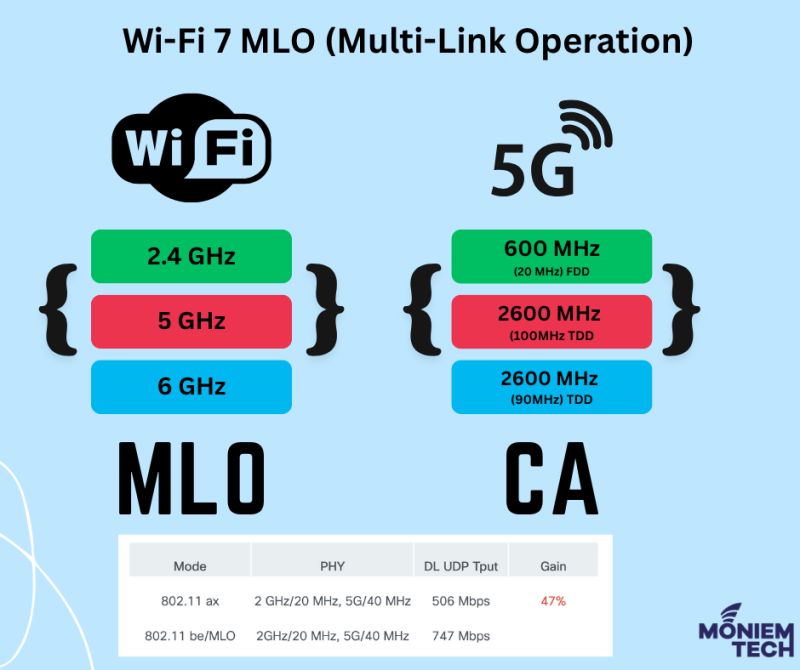
Existing Wi-Fi 6 devices support multiband operations across the 2.4 GHz, 5 GHz, and 6 GHz bands. However, these operations are independent, lacking coordination and significantly reduce efficiency. To address […]
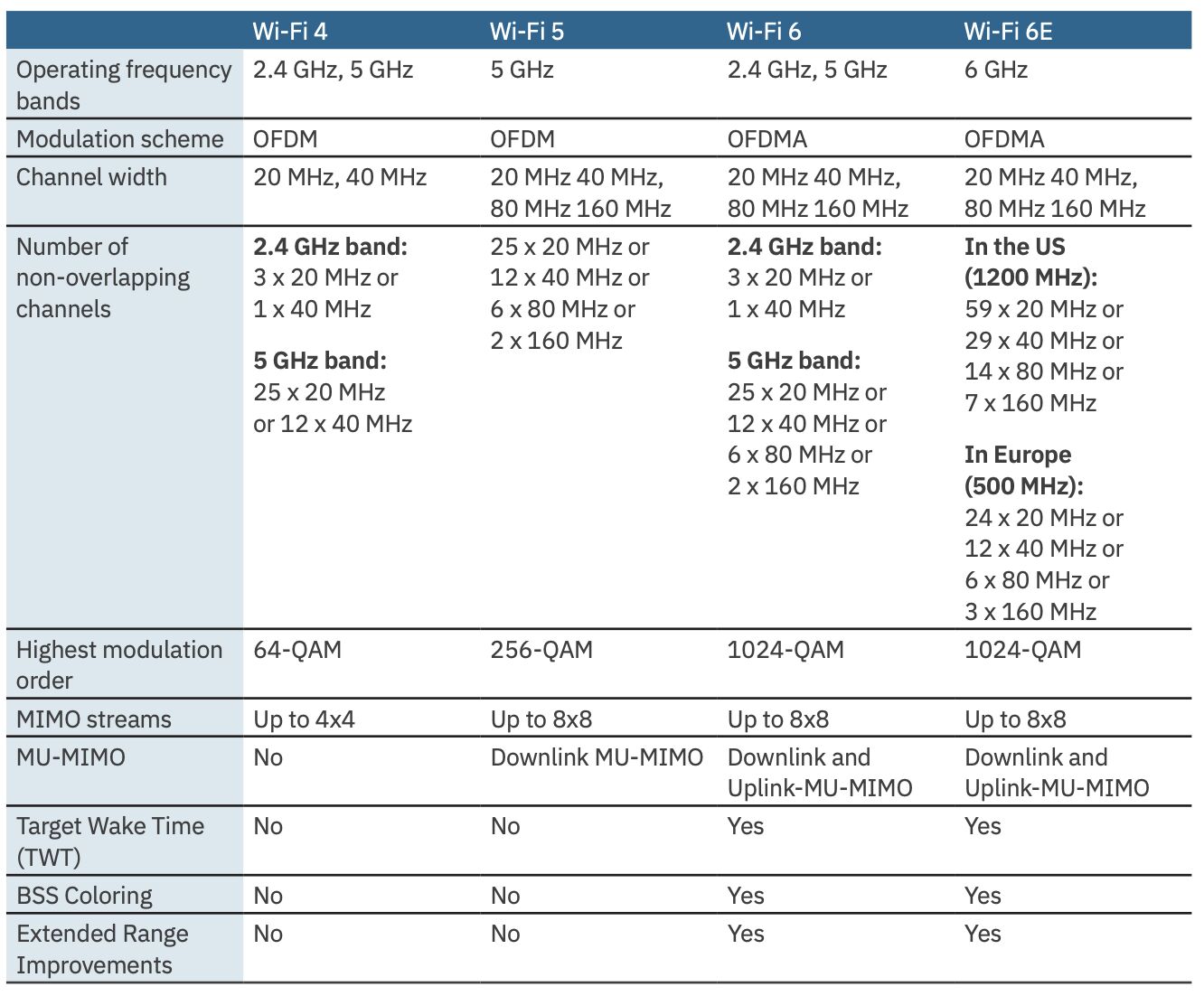
Wi-Fi remains the default solution for indoor connectivity, handling the majority of data traffic across smartphones, tablets, and IoT devices. According to the UK telecoms regulator Ofcom, in its 2022 […]
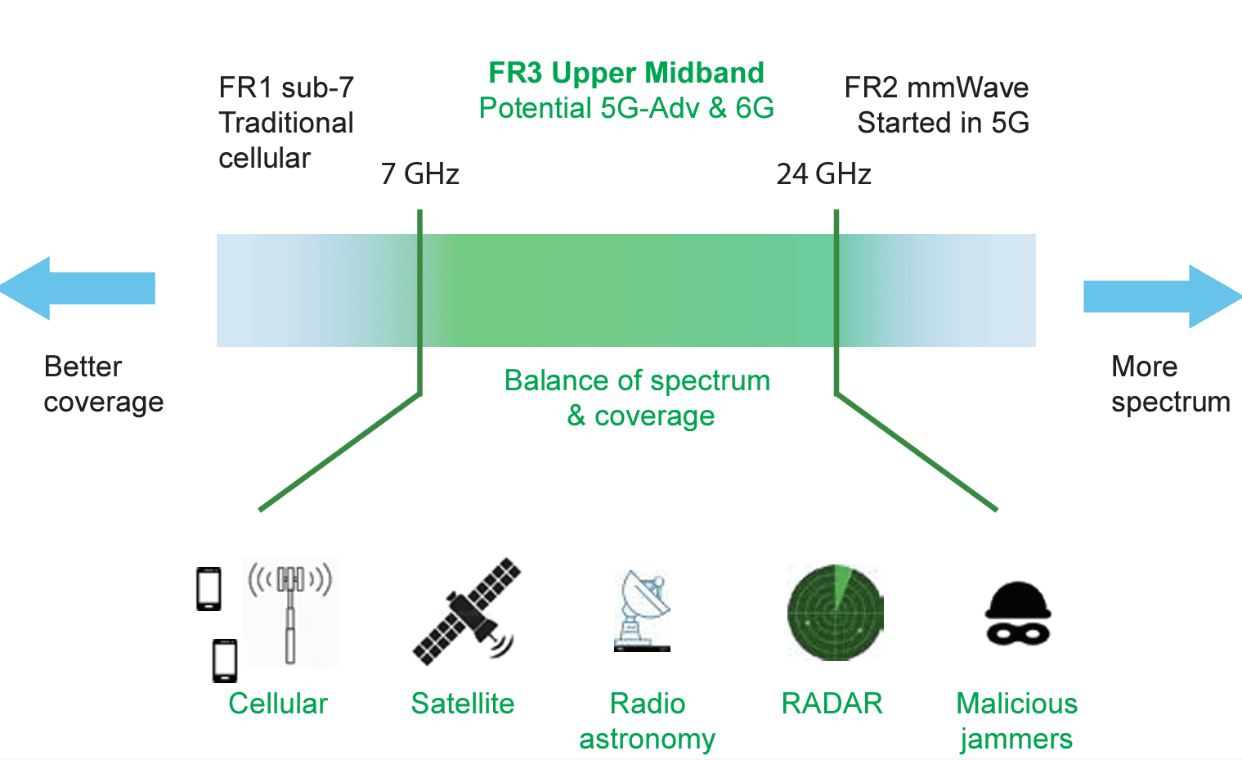
Recently, I have read an interesting white paper from Anritsu, which covered trends in wireless frequency band allocation for 5G-A and 6G. The most recent WRC was held in Dubai, […]

If you’re living in the UAE, you’ve probably noticed the new billboards across the streets promoting the latest evolution of 5G technology. Etisalat is calling it 5.5G (5G-Advanced) while DU […]

mmWave offers the fastest 5G speeds available today; however, its use cases are currently limited. With its extremely short range and poor penetration through obstacles, mmWave mainly makes sense in […]
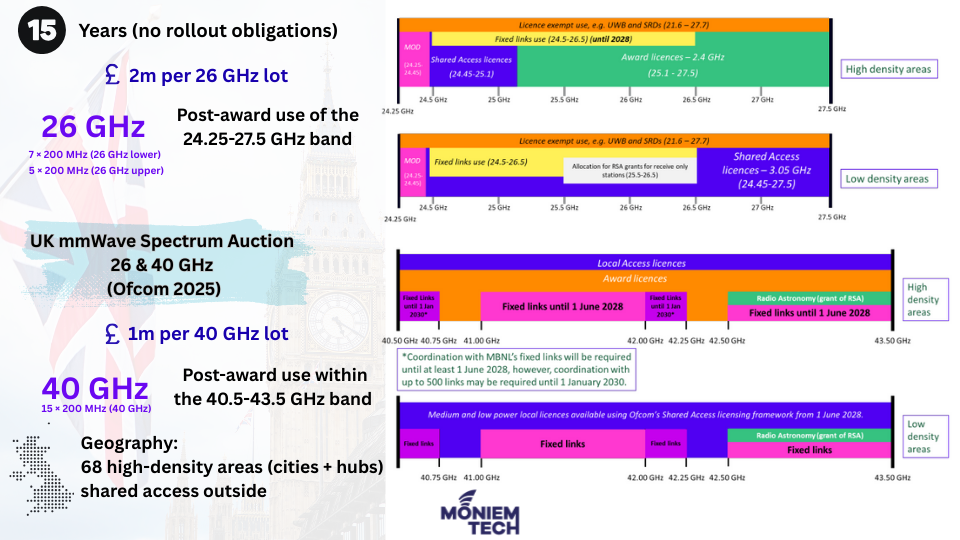
Ofcom is auctioning a total of 5.4 GHz of mmWave spectrum across the 26 GHz and 40 GHz bands. This marks a significant milestone for 5G evolution in the UK […]
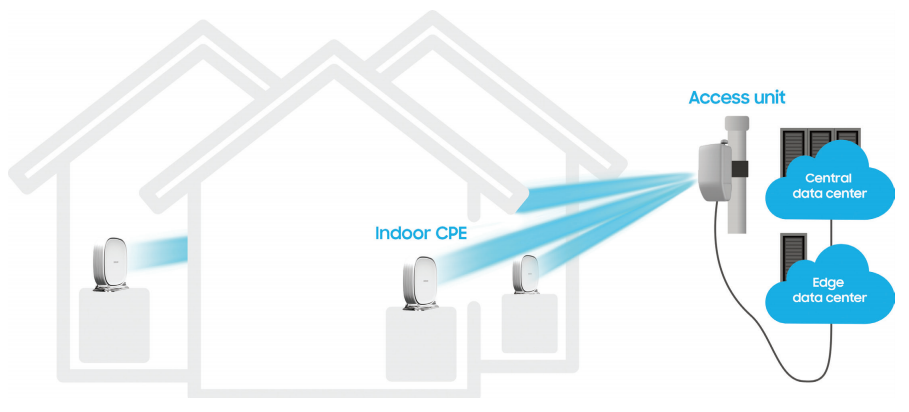
5G FWA isn’t just a “nice-to-have” – it’s the future of home connectivity. The latest data from CTIA shows a clear trend: 5G FWA is driving nearly all new broadband growth […]
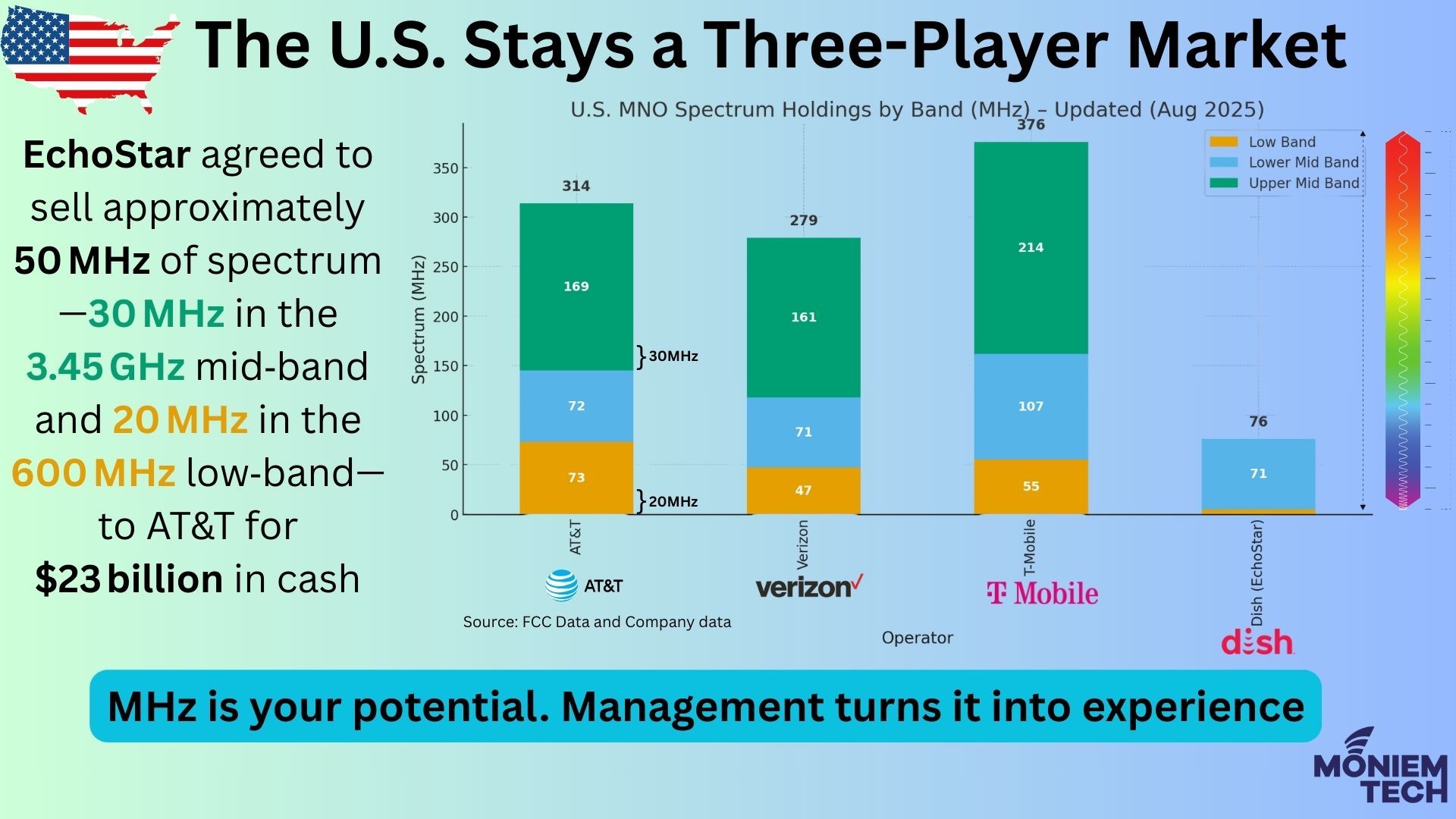
For many years, policymakers, regulators, and industry observers maintained expectations for a fourth national wireless carrier to contend with AT&T, Verizon, and T-Mobile. This anticipation primarily relied on DISH Network, which […]
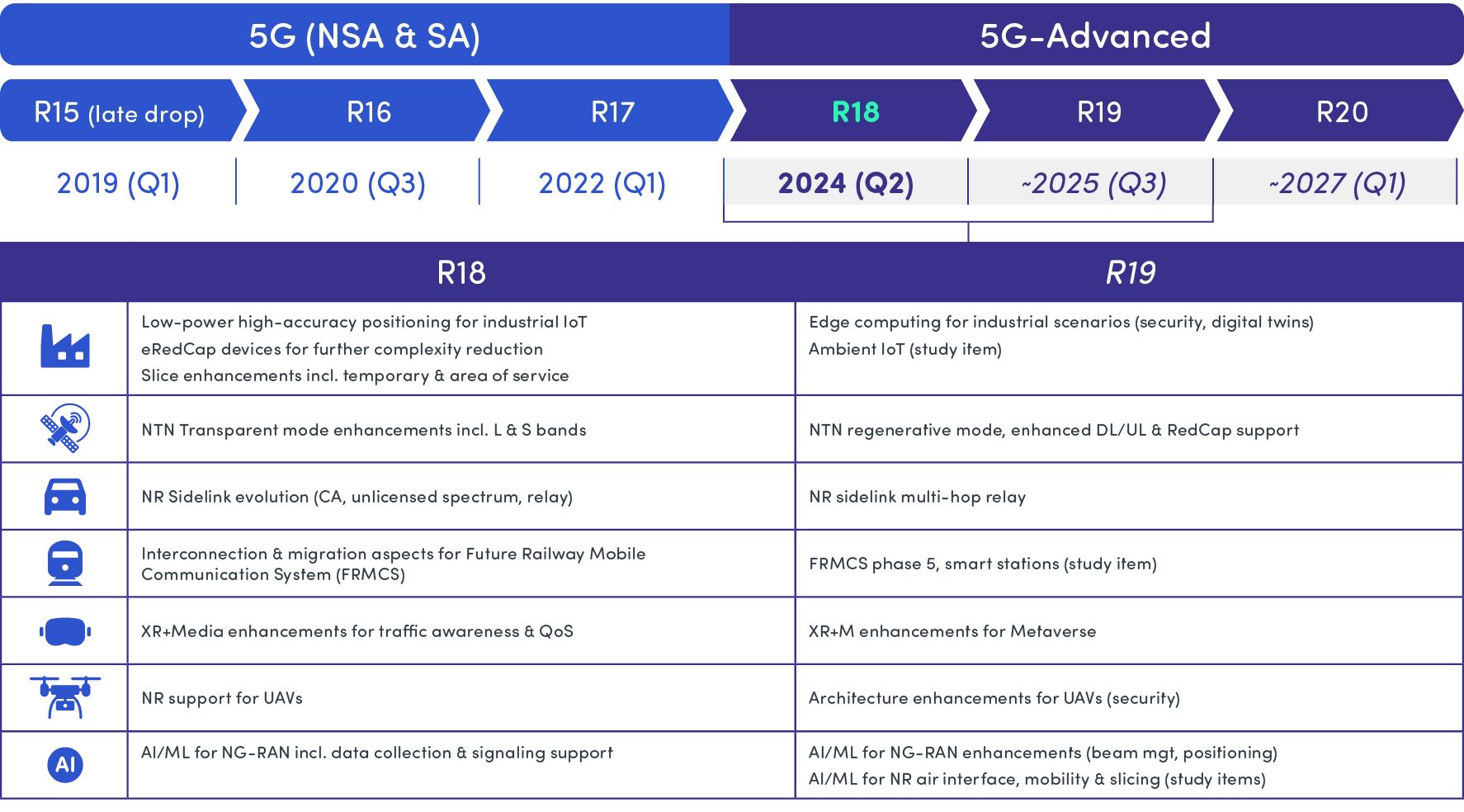
The recent Spirent article rightly highlights the potential of 5G-Advanced (5G-A) and the role of the 5G Core in enabling monetization. However, 5G-A should be seen primarily as a future-oriented […]
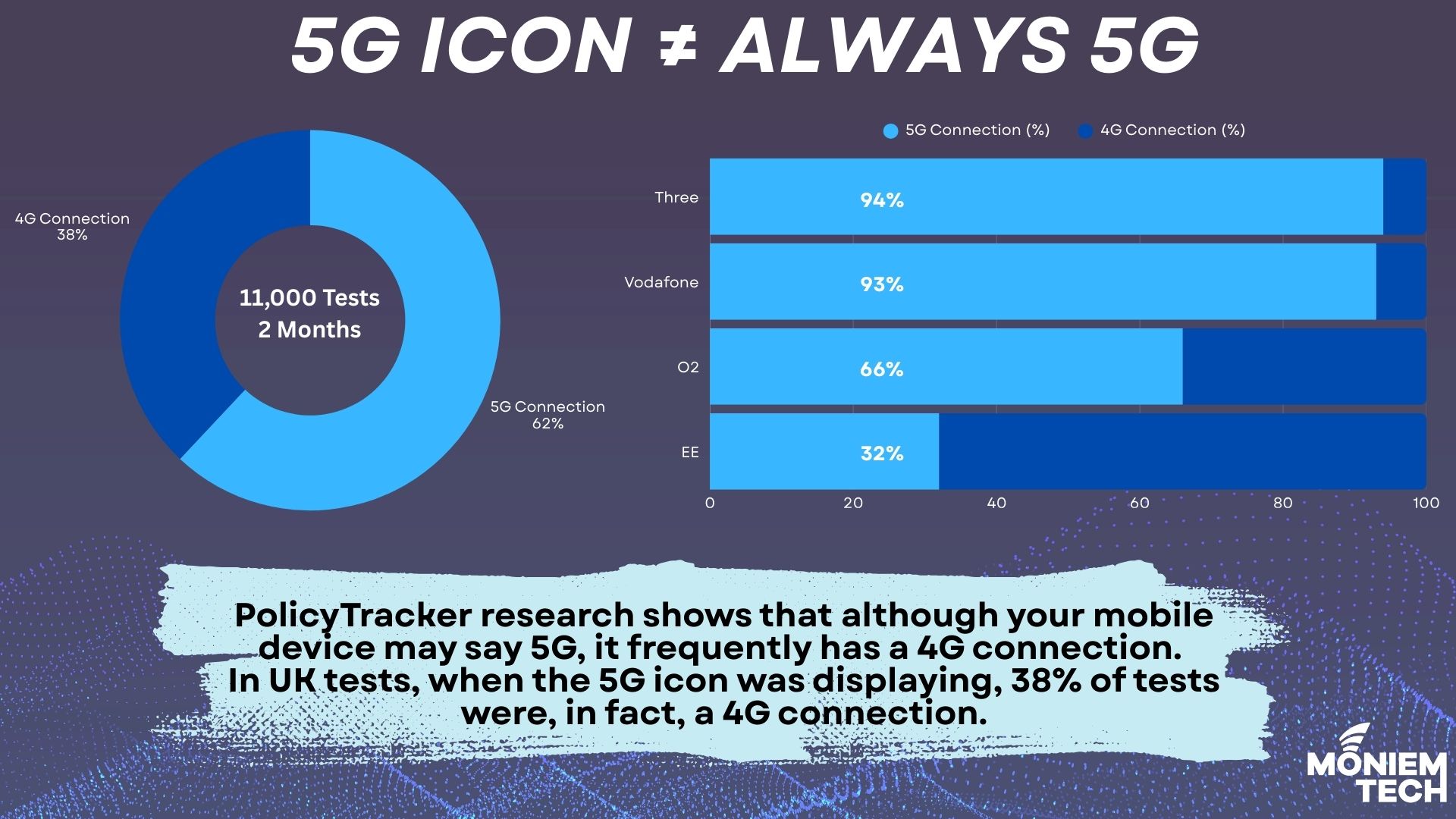
The question is: Actual 5G or Icon-only 5G. A study based on the mobile app SignalTracker shows that nearly 40% of 5G connections are actually 4G, as per PolicyTracker. Actual […]
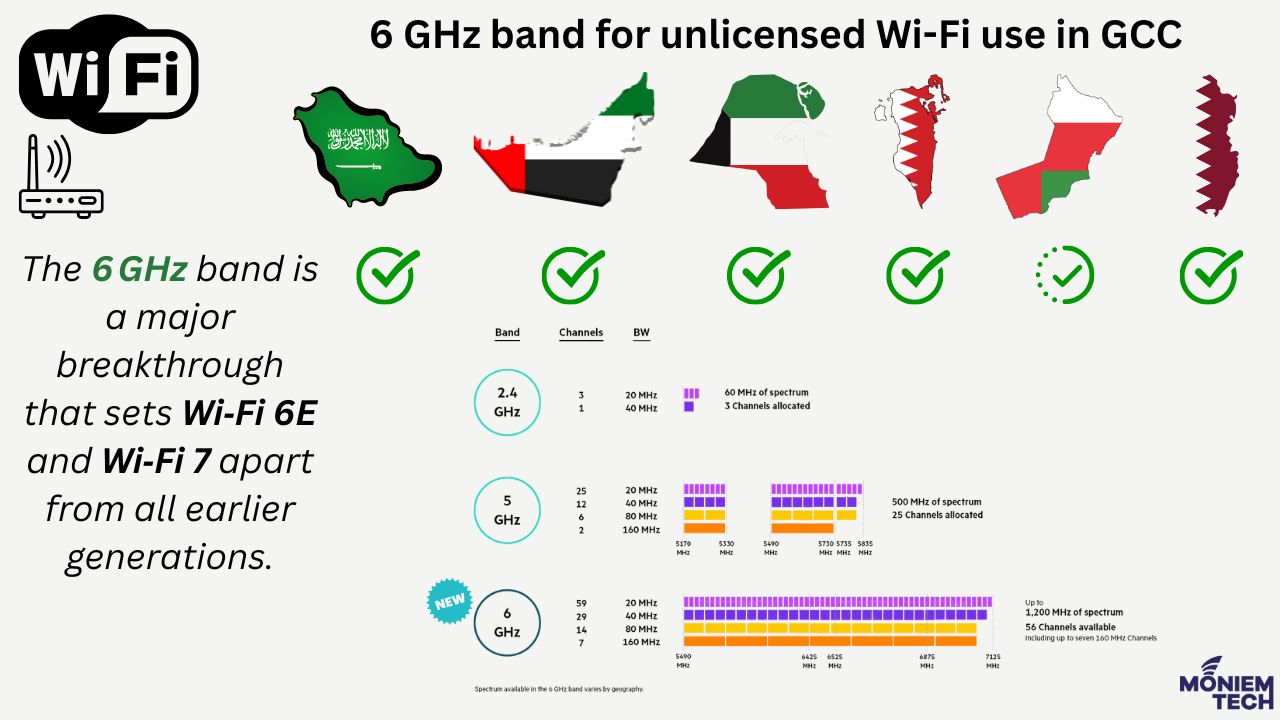
Wi-Fi is a key resource in the world communications ecosystem. Up to 90% of all mobile device traffic is carried on Wi-Fi. The 6 GHz band is a breakthrough that sets […]
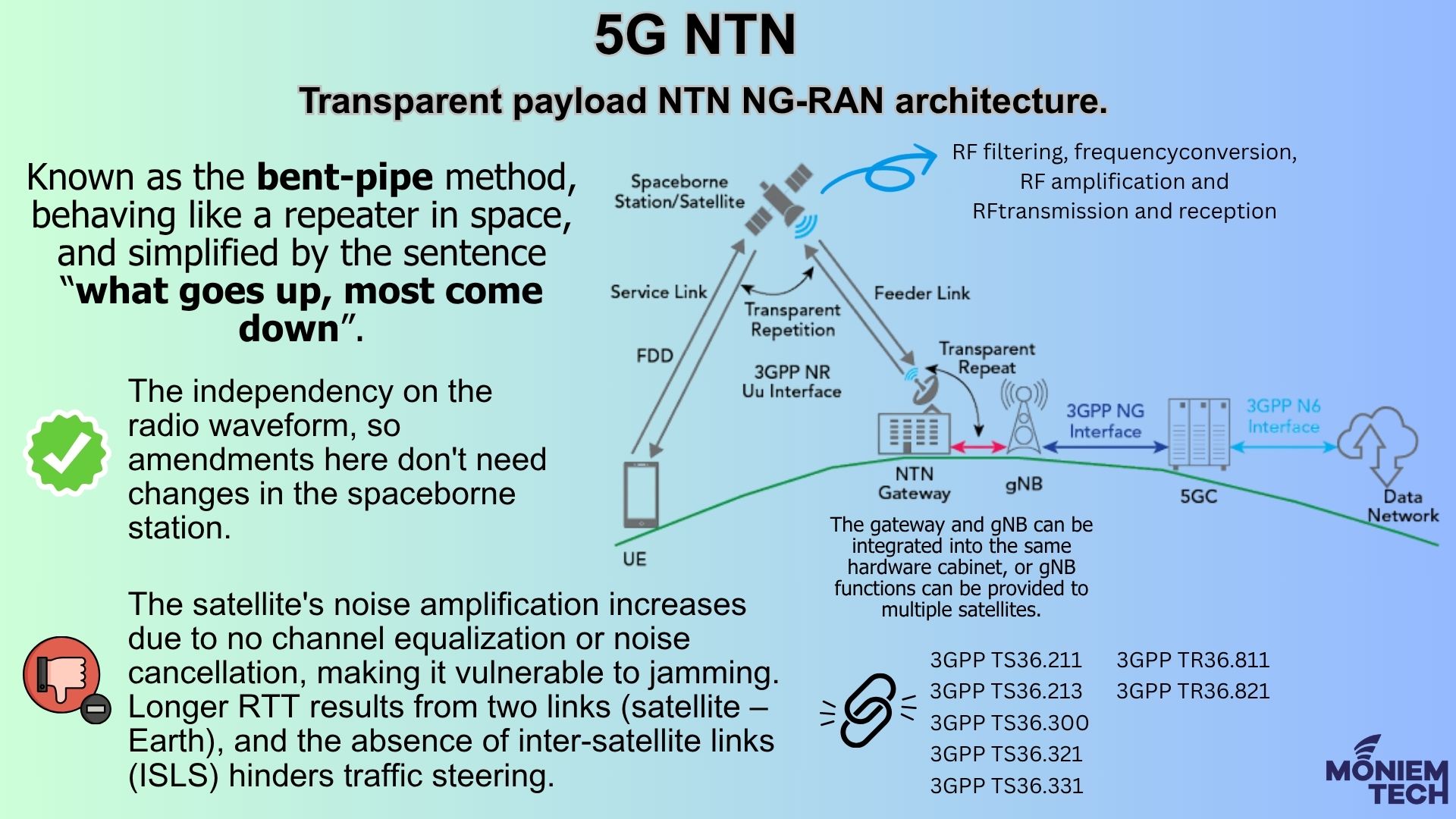
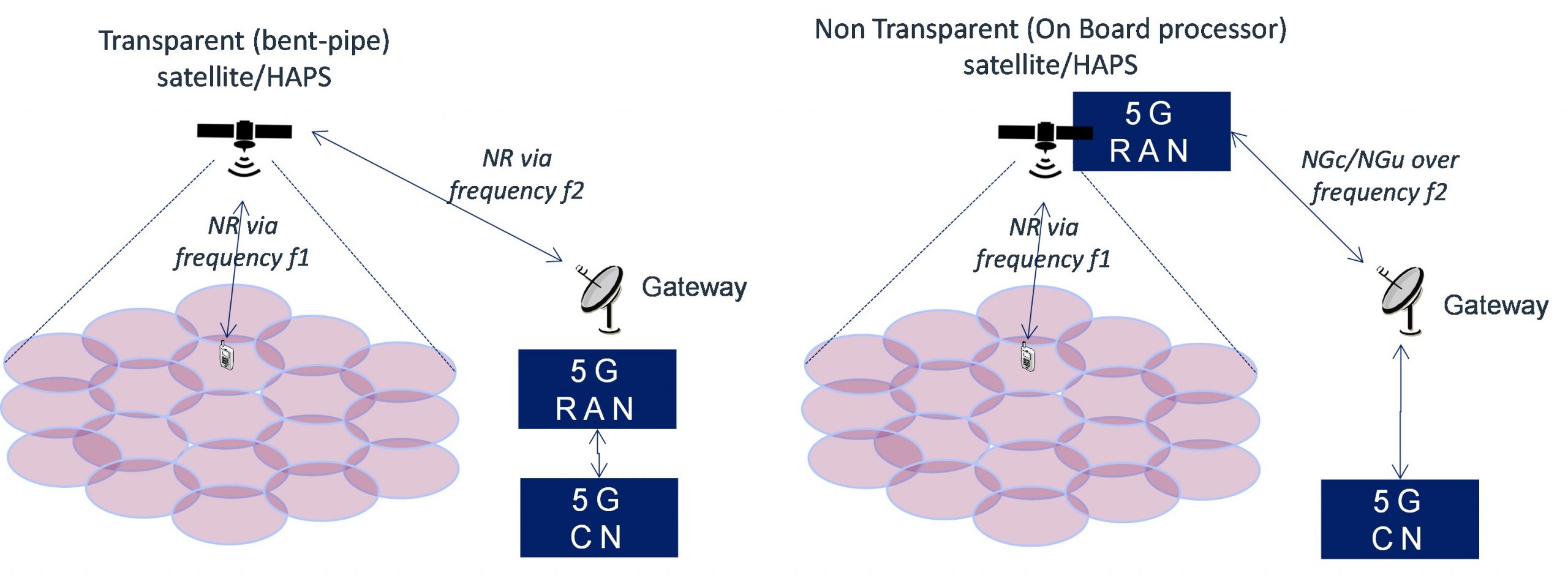
When discussing 5G NTN, it’s important to understand what NTN is, how it functions, and the purpose of Transparent Architecture. What is 5G NTN? 5G NTN refers to the integration […]
Before the advent of Rel.17, IoT deployments were plagued by connectivity challenges, especially in remote and rural areas. Terrestrial networks often fall short in providing reliable coverage, resulting in data […]

Imagine being able to download every HD video on Netflix in just one second… Now, with Japan, we can say yes. Japan’s National Institute of Information and Communications Technology (NICT) achieved […]

The upcoming Android 16 release introduces a critical new security feature: Network Notification Warnings This enhancement is designed to alert users in real time when their mobile devices are exposed […]
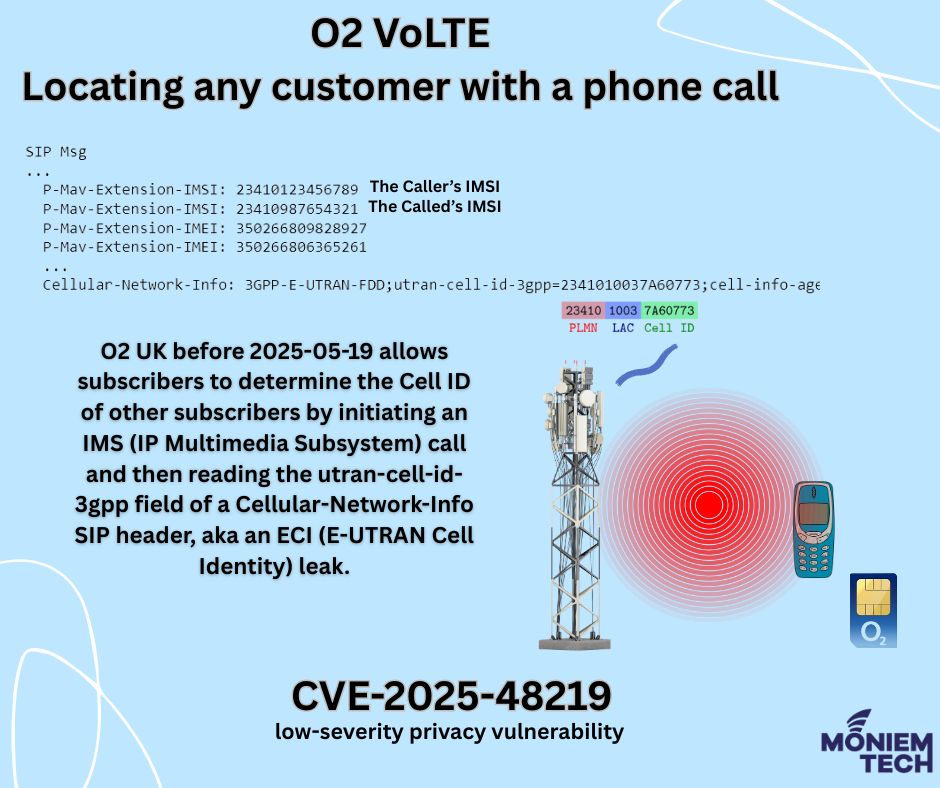
Vulnerability Details: CVE-2024-53026. It is a vulnerability affecting O2 UK’s VoLTE/IMS service, disclosed in mid-May 2025. Rated Low, with a CVSS v3 score of 3.5. It has a limited impact on confidentiality […]
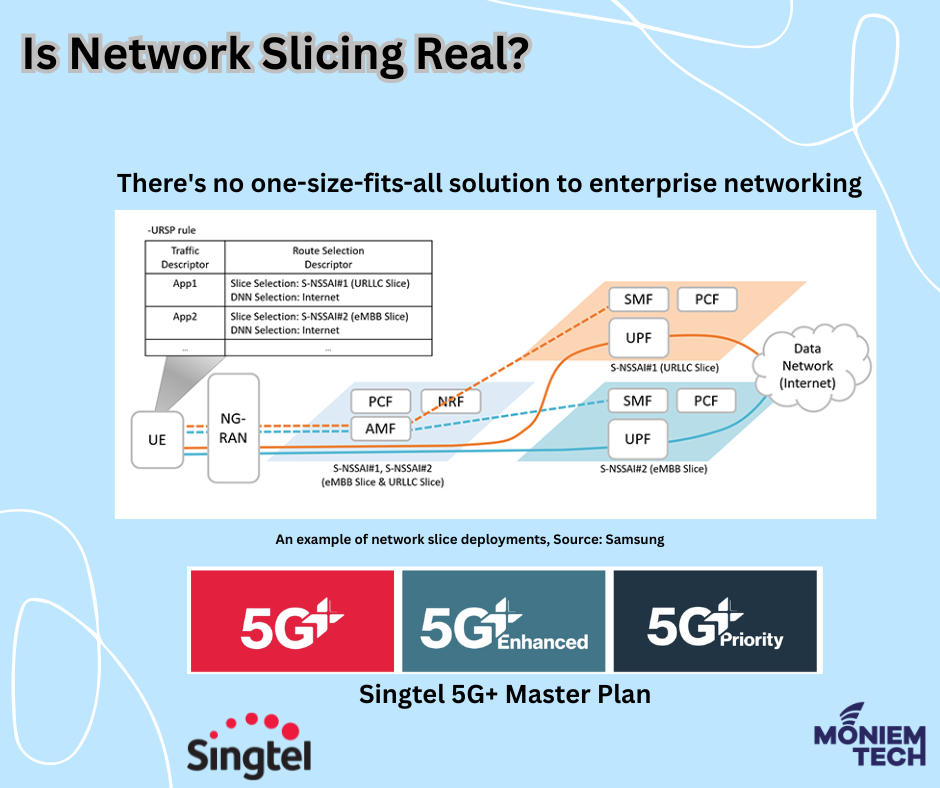
Network Slicing is essentially the ability to divide your network into individual use cases, each tailored to provide specialised services. Traditionally, in 4G, the APN (Access Point Name) was probably […]
