The journey started with 2G and 3G, where Voice was the leading service, and the main protocols were SS7 and SIGTRAN (Signaling Transport). At this time, the primary Firewalls are: SS7/SIGTRAN Firewall: Its functions are national/international interconnect protection with different policies and detection patterns in real-time. GTP Firewall: The functions are GTP Packet binary checks […]
Before discussing why we need an SMS Router, let’s understand the 1st figure when the mobile device sends SMS to another Mobile through the normal scenario without an SMS Router which means the communication is between SMSC and HLR. The Normal Scenarios for Sending SMS: The mobile sends the SMS to the SMSC. Since the […]
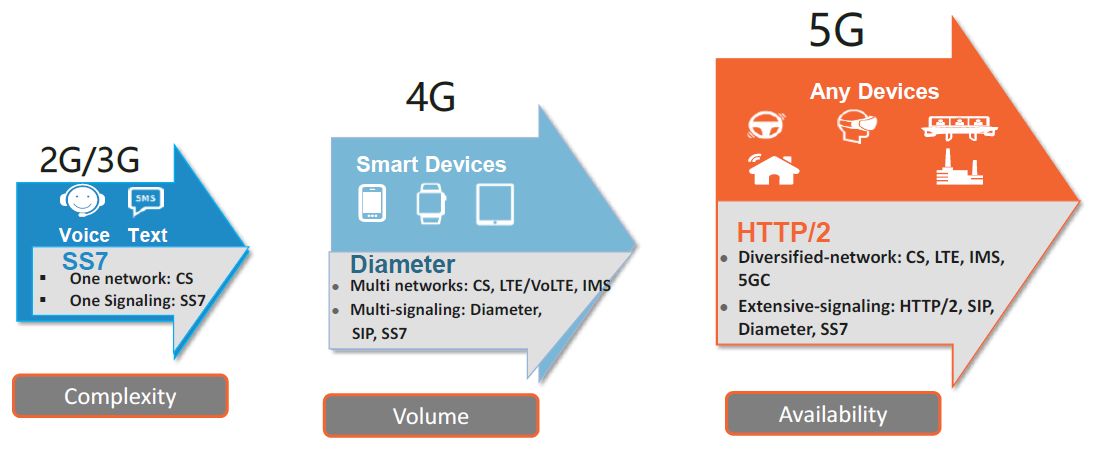
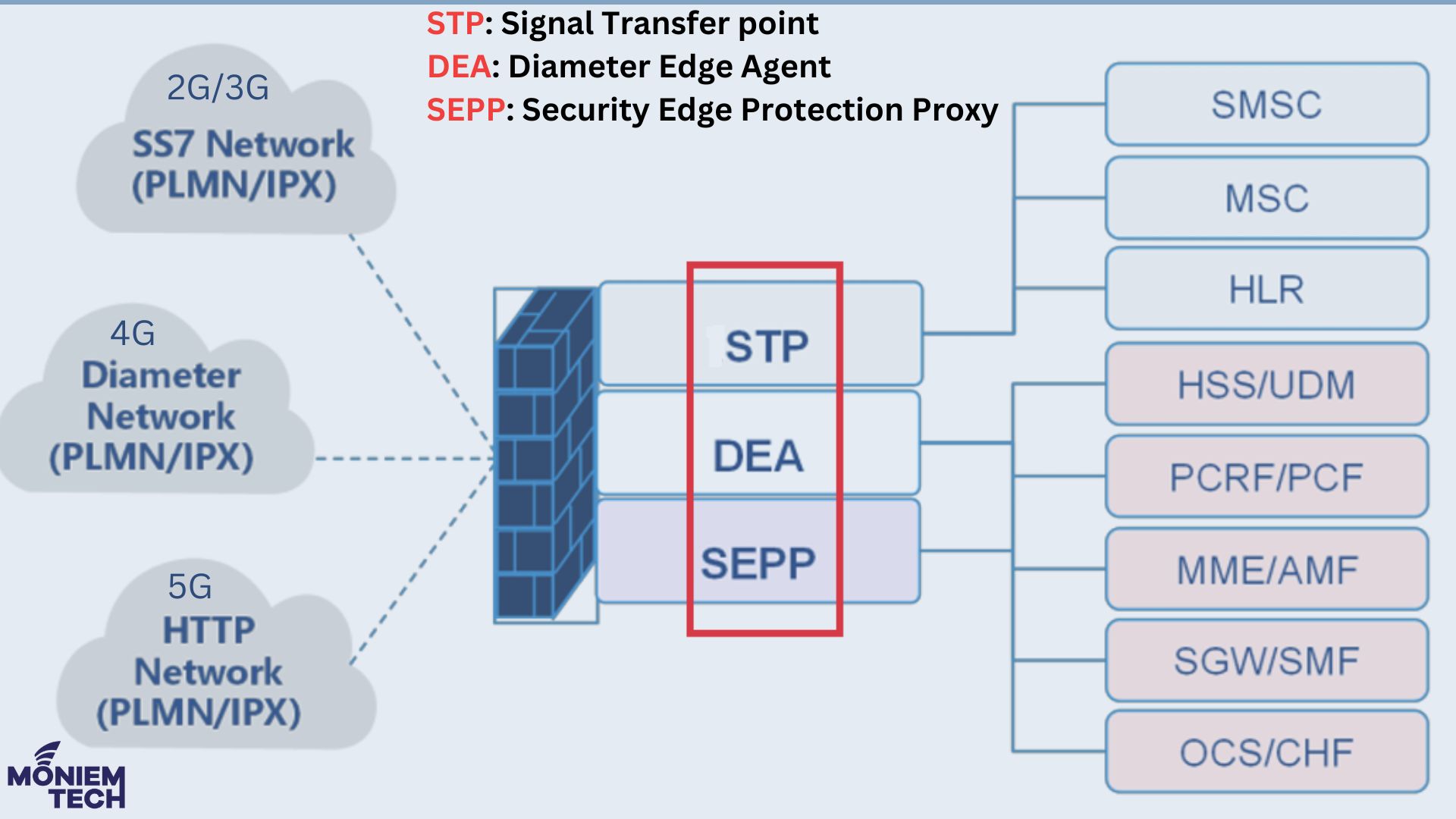
📃In 2G and 3G, voice and text were the main services based on SS7 signaling. In these networks service availability was the priority. The Signal Transfer Point (STP) was the node that routed signaling messages. 📃In 4G, networks became data and media-centric and needed signaling to support smartphones and Apps. Signaling volume grew to support […]

Before starting to talk about IMSI Catcher, we need to understand what is the IMSI, its importance, and its structure. Based on this, we will discuss the IMSI catcher. So let’s GO 🙂 What is IMSI? IMSI, International Mobile Subscriber Identity, is a unique static identity allocated to each subscriber in a mobile wireless system. […]
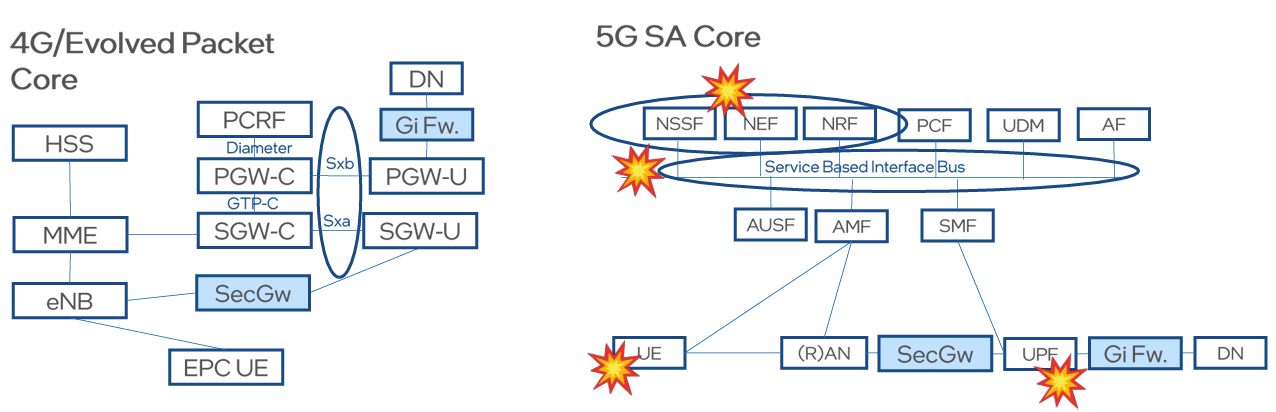
If you look at how security was addressed in the 4G core (EPC), you had perimeter devices, whether it’s firewalls, security devices that protect from denial of service attacks, or just security gateways at the periphery, and you had fewer vendors addressing the core infrastructure. So, if you have a single core vendor, the risk […]
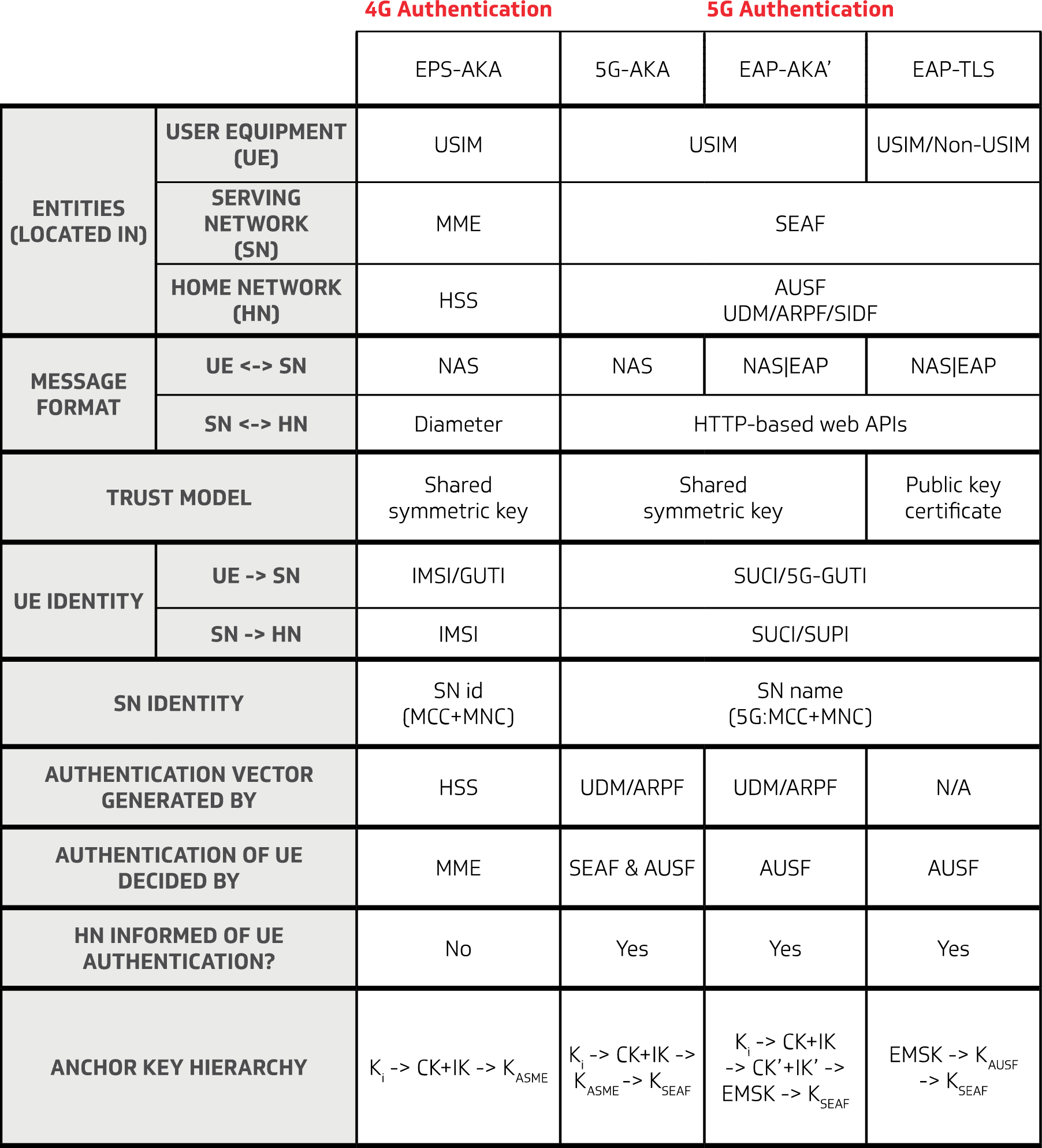
The authentication procedure in 3GPP 5G security has been designed as a framework to support the Extensible Authentication Protocol (EAP) – a security protocol specified by the Internet Engineering Task Force (IETF) organization. This protocol is well established and widely used in IT environments. The advantage of this protocol is that it allows the use […]

5G Timeline and Standardization During preparation, it was decided to split Phase 1 into two parts. In December 2017, standardization of the non-autonomous, or Non-Standalone, architecture for 5G New Radio (NR) was completed. This first official set of 5G standards defines the wireless air interface for interworking with existing LTE-based networks. This has allowed operators […]

Introduction 5G will give a diverse and new set of services and use cases affecting nearly every aspect of our lives. But to exceed all expectations, 5G-enabled services and applications must be delivered securely. For example, 5G will support Massive Internet of Things (MIoT) implementations like traffic sensors and Vehicle-to-Infrastructure (V2I) services that are the […]
