Introduction
5G will give a diverse and new set of services and use cases affecting nearly every aspect of our lives. But to exceed all expectations, 5G-enabled services and applications must be delivered securely.
For example, 5G will support Massive Internet of Things (MIoT) implementations like traffic sensors and
Vehicle-to-Infrastructure (V2I) services that are the cornerstone for future smart cities. It’s critical that hackers cannot access that information.
Security has always been a top architectural priority in all previous mobile generations. For instance, Third Generation Partnership Project (3GPP) Release 8 has added a variety of advanced security/authentication mechanisms through nodes such as the services capability server, and after that Release 11 provided additional capabilities to support secure access to the core network. These and more additions in the 4G era are noticeable because LTE is the base for 5G, which includes the security mechanisms.
5G creates new cyber security considerations. 5G’s use of the cloud and edge computing and traditional IT networks and convergence of mobile creates new attack vectors.
5G Attacks Types
- Zero-day attacks: threats that don’t already have either previous history or a fingerprint (signature).
- Day-one attacks: threats that already have a signature or fingerprint and routinely there is a mitigation
strategy in advance to stand against the attack.
Why Security Is Important Factor in 5G?
5G is the first mobile technology created to meet the unprecedented requirements of connected cars, connected cities (smart cities), connected homes (smart homes), wearable, health care devices/applications, smart
appliances and other IoT devices and services.
Example: IoT Market
Many of the “things” that create the IoT architecture are objected to zero-day attacks, which are security gaps in software discovered by the hackers and are unknown to vendors yet. The 5G evolution means billions of these things, collectively referred to as MIoT, will be using the 5G Radio Access Network (RAN).
5G Security Vision
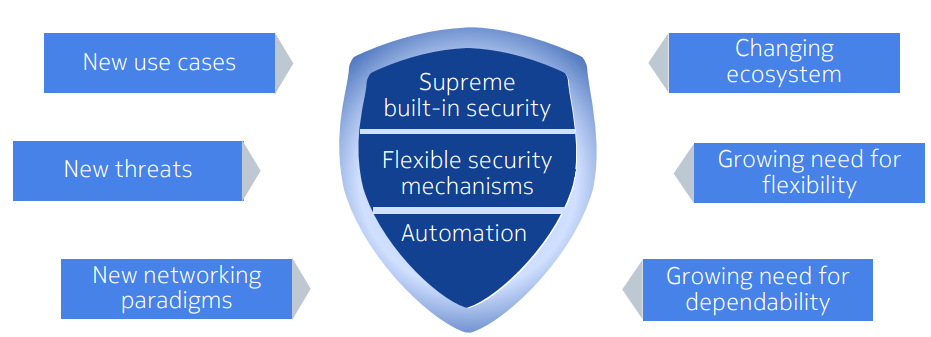
- Higher Level of Security
• Increased robustness against cyber attacks.
• Enhanced privacy.
• Security assurance. - Higher Flexibility in the Selection of Security Mechanisms
• Alternative identification and authentication procedures.
• User plane encryption and integrity protection upon-request to use.
• Adjust security mechanisms per network slice. - Higher Degree of Security Automation
• Holistic security orchestration and management.
• Self-adaptive, intelligent security controls.
The Main Security Enhancements in 5G
• Secure communications, encryption and integrity protection mechanisms are used in 5G to protect the user plane, control plane, and management traffic.
• Unified authentication structure for the different 5G access technologies and devices.
• User privacy protection for the data that can be used by unauthorized persons to identify and track subscribers (for instance, protecting permanent identifiers such as SUPI, IMSI, and IMEI).
• Secure Service Based Architecture and slice isolation that allow various services and applications to implement optimized security mechanisms and block attacks from reaching to other slices.
• RBS detection and mitigation techniques, using radio-reporting analytics and UE-assisted RBS-detection mechanisms.
Conclusion
5G may be deemed as evolutionary in the era of cellular technology generations. However, the main functions and
frameworks used in previous generations (3G, 4G) will continue to work under the 5G umbrella.
For instance, the 5G Radio (NR) can be “plugged” into a 4G core, a compatibility element that did not exist in 3G or 4G radios, and at the same time co-exist with 4G radios as part of the overall network.
References:
- Nokia White paper.
- 3GPP.
