If you look at how security was addressed in the 4G core (EPC), you had perimeter devices, whether it’s firewalls, security devices that protect from denial of service attacks, or just security gateways at the periphery, and you had fewer vendors addressing the core infrastructure. So, if you have a single core vendor, the risk is relatively smaller, there were proprietary interfaces, and then you had hardware security modules provided by the vertical vendor community. So, It’s limited in threats.
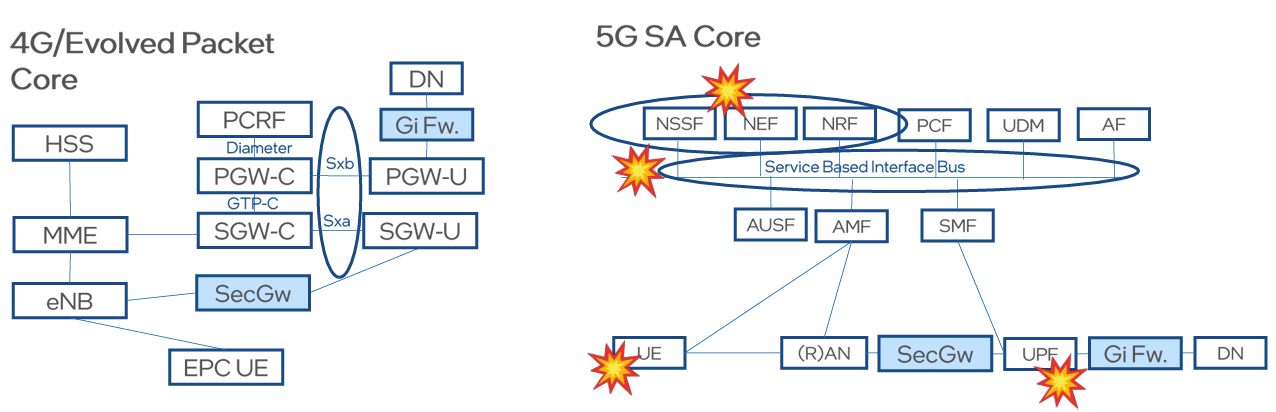
However, The dynamics are completely different as we go into the 5G SA Core and the question now is Why?
First of all, the architecture is a service-based architecture (SBA). You have the 5G control plane on a single service-based interface bus, which means a single network function that gets attacked exposes the entire core. Not only that, you have web-based APIs, cloud-native infrastructure, microservices deployment, you have multi-domain deployments. It’s a highly distributed edge. So, now you are going beyond the perimeters of telco infrastructure and deploying solutions in areas where you don’t have necessarily the confirmation on their security profile. So, it’s unsecure locations that you may be deploying your solutions in.
