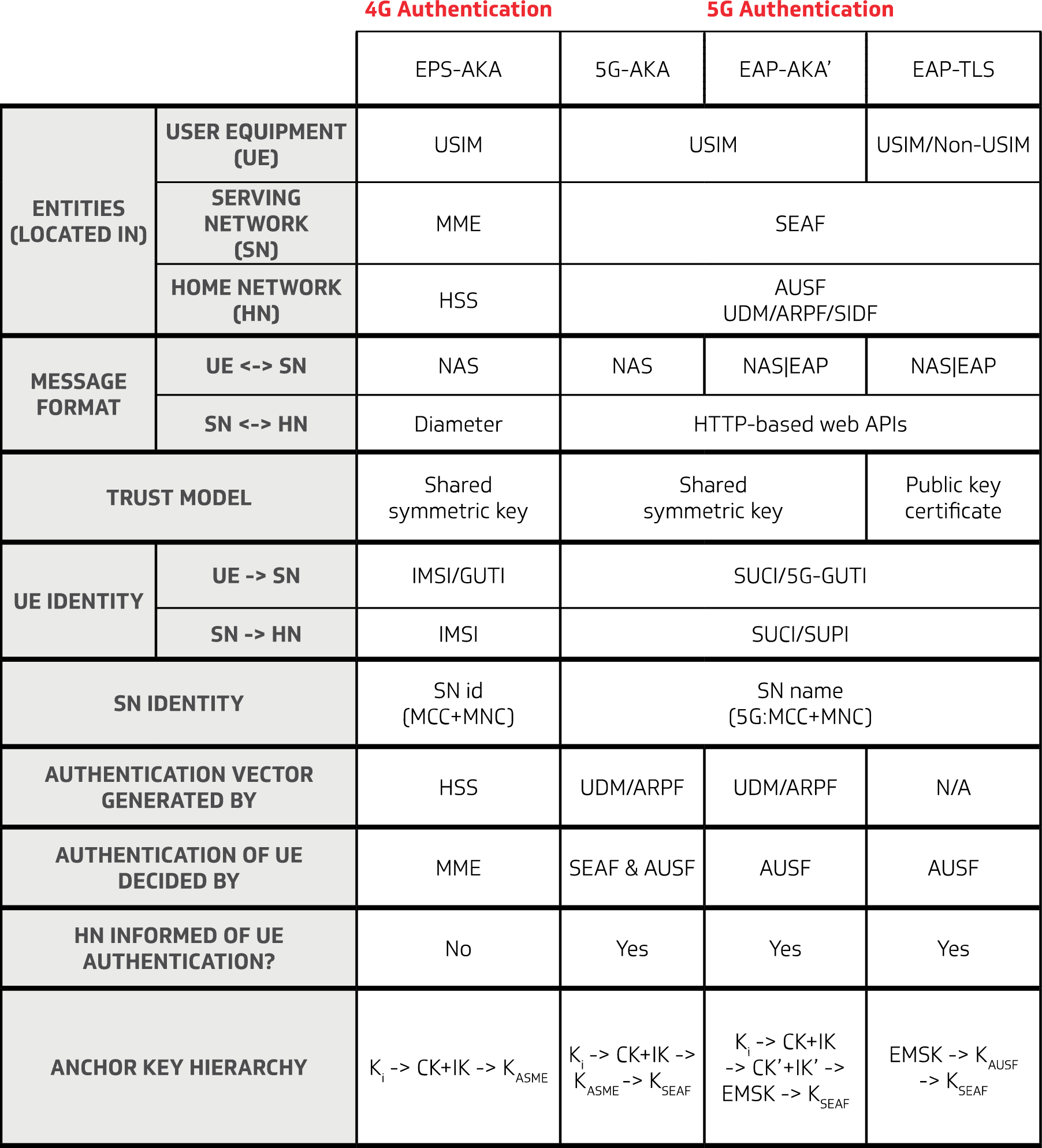
The authentication procedure in 3GPP 5G security has been designed as a framework to support the Extensible Authentication Protocol (EAP) – a security protocol specified by the Internet Engineering Task Force (IETF) organization. This protocol is well established and widely used in IT environments.
The advantage of this protocol is that it allows the use of different types of credentials besides the ones commonly used in mobile networks and typically stored in the SIM card, such as certificates, pre-shared keys, and username/password. This authentication method flexibility is a key enabler of 5G for both factory use-cases and other applications outside the telecom industry.
The support of EAP does not stop at the primary authentication procedure, but also applies to another procedure called secondary authentication. This is executed for authorization purposes during the set-up of user plane connections, for example to surf the web or to establish a call. It allows the operator to delegate the authorization to a third party.
The typical use case is the so-called sponsored connection, for example towards your favorite streaming or social network site and where other existing credentials (e.g. username/password) can be used to authenticate the user and authorize the connection. The use of EAP allows to cater to the wide variety of credentials types and authentication methods deployed and used by common application and service providers.
3GPP defined EPS-AKA for 4G LTE and similarly for 5G following three authentication methods are defined
- 5G-AKA: 5G-Authentication and Key Management
- EAP-AKA: Extensible Authentication Protocol – Authentication and Key Management
- EAP-TLS: Extensible Authentication Protocol – Transport Layer Security