The SS7 network was once considered an environment that controls users’ access to network-based content and services, allowing licensed mobile operators to access customer data. However, many unlicensed entities currently have access to the SS7 network, taking advantage of the low security of this protocol. Consequently, more businesses and individuals with direct access to the network, as well as intermediaries, are selling their access on the dark web.
For $150–$2500, a hacker can gain unauthorised access to the SS7 network and exploit cellular vulnerabilities without requiring any infrastructure at all.
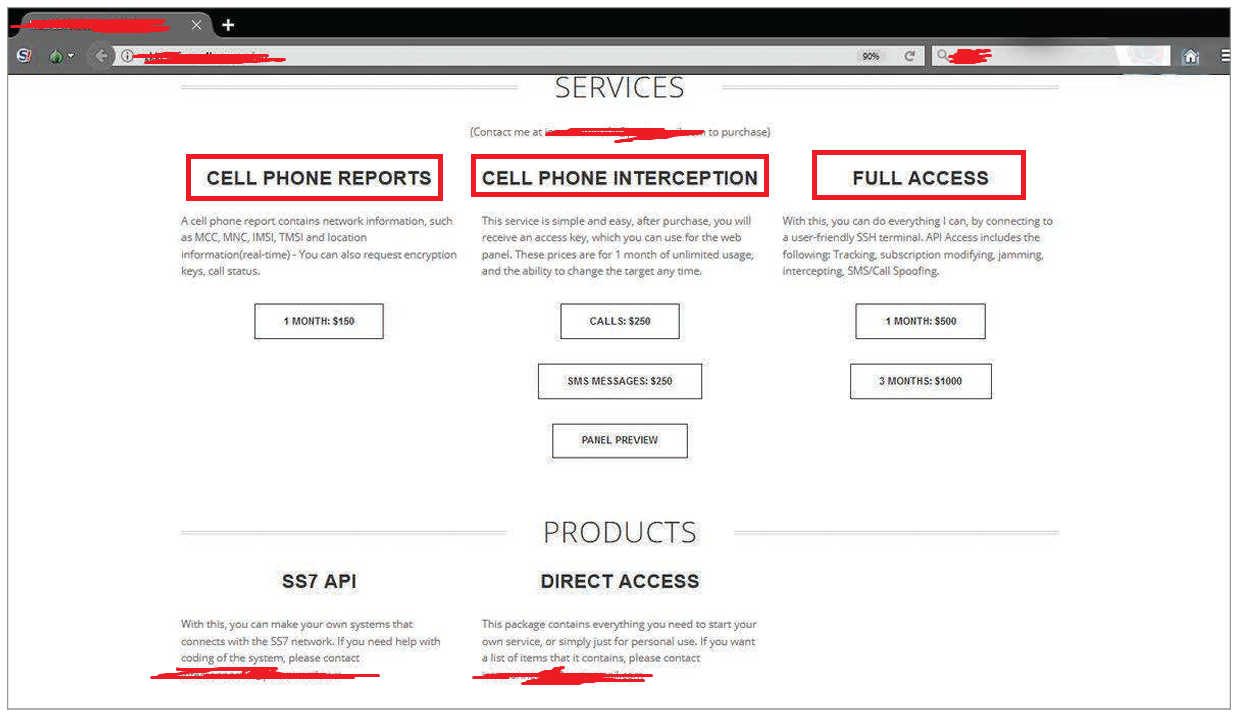
Example, A dark web site selling SS7 access which includes:
- Cell Phone reports, including IMSI, IMEI, TMSI, and location information.
- Cell Phone interceptian.
- Full access, including SMS and call spoofing.
But What is the solution?
The first step in improving signalling-related security is to evaluate the state of the network by monitoring SS7 traffic for potential attacks and classifying incoming MAP messages arriving on the interconnection interface. This also involves configuring an SS7 firewall or an edge node to prevent unauthorised messages and attacks from reaching the core network.
Useful Documents to Read from GSMA Recommendation
- FS.11: SS7 interconnect security monitoring guidelines.
- FS.07 SS7 and SIGTRAN network security.
- IR.82 security SS7 implementation on SS7 network guidelines.
- IR.88 LTE and EPC roaming guidelines.
