Last weekend, by coincidence, I found a fraud story related to the Telecom domain called “Spoofing CLI” or “Calling Line Identification (CLI) spoofing.” which is a technique used in mobile network fraud where the caller purposefully fakes the phone number or the caller ID information that appears on the recipient’s device.
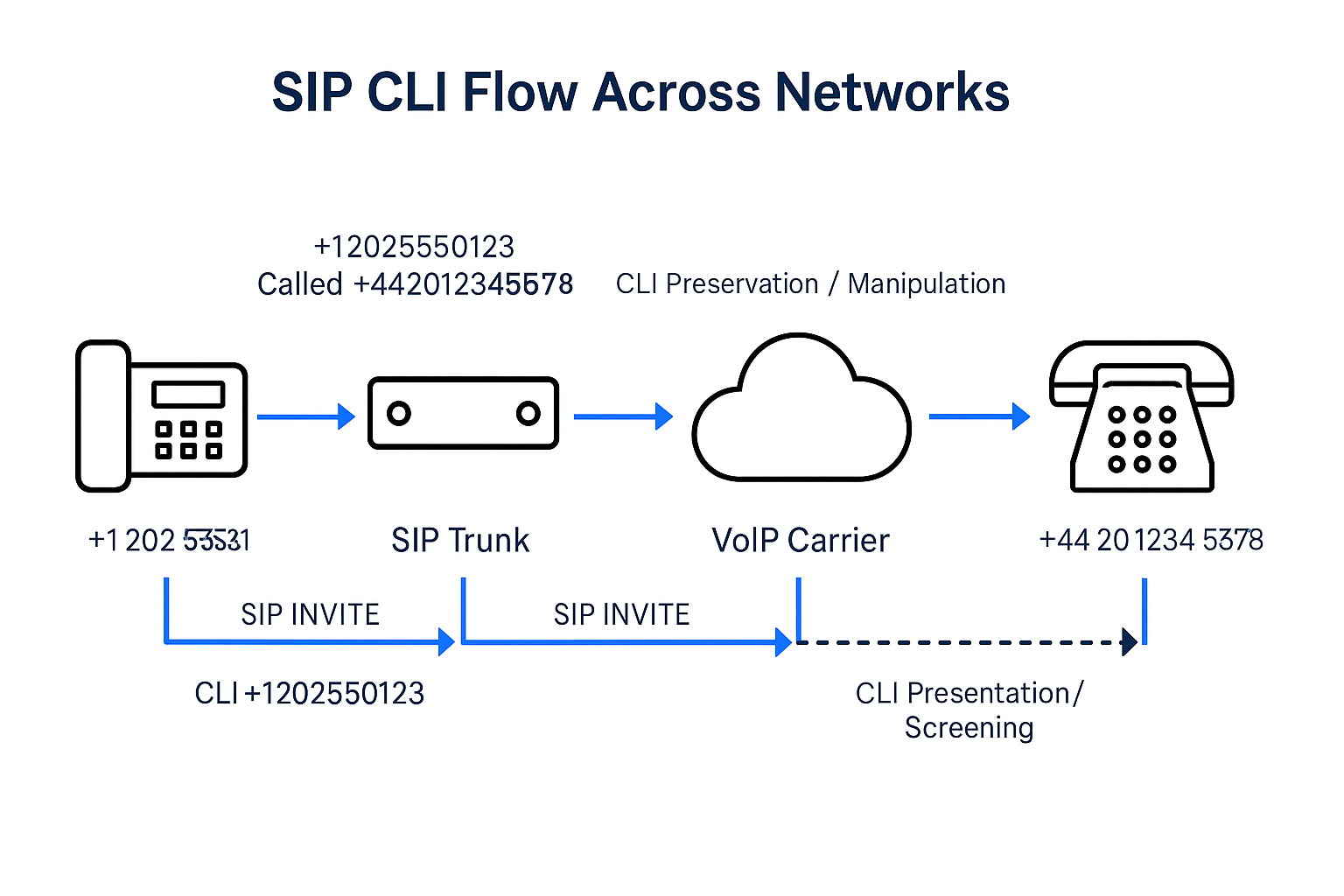
CLI is the phone number that appears on the recipient’s caller ID when they receive a call. Here’s how it applies specifically to international calls. It displays the number of the caller (usually in E.164 format, like +44 for the UK or +1 For the US, it helps the recipient identify the source of the call and is used for transparency, billing, fraud detection, and regulatory compliance.
Spoofing is typically done by manipulating the data transmitted to the recipient’s phone when a call is made. Across both local and international attacks, the goal of CLI spoofing can vary, but common motivations include:
- Hiding the real identity: The caller might want to conceal their actual phone number, often for privacy reasons.
- Impersonation: In some cases, attackers use CLI spoofing to impersonate a trusted entity, such as a bank, service provider, or company, to carry out social engineering, phishing attacks, or fraudulent activities.
Let’s now jump to the story I read last weekend about a person named Tejay Fletcher, who is the owner of the website iSpoof, which was a website owner that offered services to spoof caller IDs, allowing users to disguise their phone numbers to appear as if they were calling from a legitimate organization like a bank, police, or government agency.
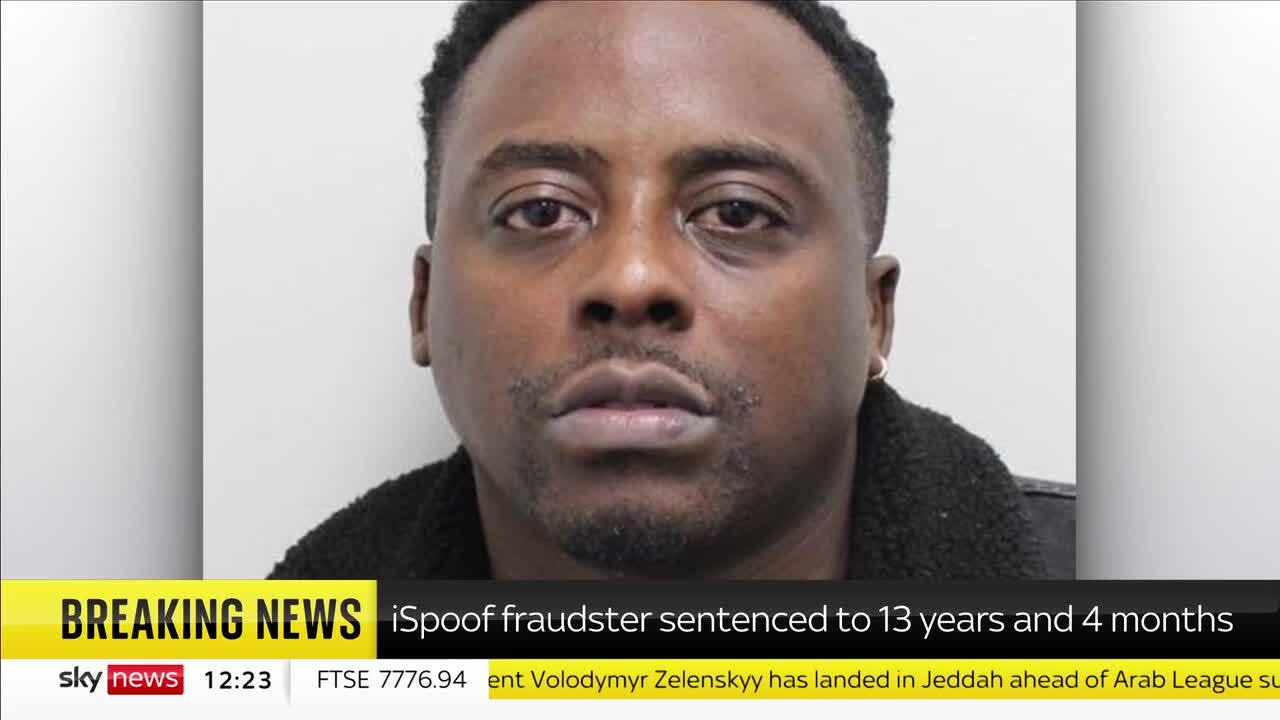
iSpoof was widely used for fraud and phishing scams, allowing criminals to trick victims into giving up their personal and financial information. Fletcher spent time marketing #iSpoof on the Telegram Channel, The iSpoof Club, to promote iSpoof and update users on new developments and website updates.
The site was taken down in November 2022 by international law enforcement, including the UK’s Metropolitan Police and the FBI, during a large-scale cybercrime operation. Over 100 people were arrested globally, including the site’s administrator, Tejay Fletcher, who was sentenced to prison. The total losses to victims in the U.K. alone are said to be more than £48 million ($59.8 million), with confirmed global losses estimated to be at least £100 million ($124.6 million).
Detection of Suspicious Calls
A large number of mobile networks already have a signalling firewall platform deployed to combat signalling security issues and fraud. Typically, these firewalls integrate into the core network and can process and decode the full signalling stack, as well as communicate with external intelligence to analyse and detect threats. There are many techniques:
- STIR/SHAKEN (in the US and some other regions)
STIR (Secure Telephony Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using toKENs) are caller ID authentication protocols. They verify whether the phone number displayed on the caller ID matches the actual number from which the call originated. These protocols are utilized by major carriers in the US and Canada and classify calls as either “Verified” or “Spam Likely” based on this verification. - Traffic Pattern Analysis
Mobile Network Operators (MNOs) analyze call volume, frequency, and origin-destination patterns to identify red flags. Indicators of potentially fraudulent activity include:
– Thousands of calls originating from a single source in a short time frame.
– High rates of call failures or short-duration calls.
– Calls coming from VoIP sources with spoofed Caller Line Identification (CLI). - AI/ML-Based Call Scoring
Many carriers implement machine learning algorithms to assess call behaviour. These systems are designed to “learn” the difference between standard and suspicious behaviour, allowing them to flag anomalies in real-time. - Real-Time Fraud Management Systems (FMS)
Specialized systems monitor calls as they are being routed. These systems check against:
– Known fraudulent numbers (blacklists).
– Databases of spoofed numbers.
– Inconsistencies in IMSI/TMSI during mobile signalling. - Call Validation via SIM and Network Events
Suspicious calls may be linked to SIM swapping, unexpected roaming status, or changes in the IMSI, which helps identify potential fraud vectors. - Customer Feedback Loop
Many networks enable users to report spam or scam calls. This feedback contributes to:
– Shared databases (e.g., GSMA’s Fraud Intelligence Database).
– Dynamically updated blocking lists.
MNO Countermeasures After Detection
- Call labelling (e.g., “Spam Likely,” “Fraud Risk”).
- Network-level blocking before the call reaches the user’s phone.
- Alerts to customers via SMS or app notifications.
- Escalation to law enforcement for coordinated takedowns.
How to Protect Against Caller ID Spoofing
- Recognize the Signs
- Unexpected calls from banks, HMRC, or the police asking for personal info or payments.
- Being pressured to act urgently or threatened with consequences.
- Don’t Trust Caller ID Alone
- Caller ID can be faked — always be cautious even if the number looks official.
- Verify Independently
- Hang up and call the organization back using a trusted number from their website or official communication.
- Enable Call Protection
- Use a carrier or app-based call protection (e.g., Hiya, Truecaller, or your mobile provider’s anti-spam tools).
Remember, The Police will be seeing you soon ?

