One of the threats that face any cellular technology is Bidding Down or Service Degradation.
What is Bidding Down?
Hackers can use IMSI-impersonating devices to execute DoS attacks, but that’s not all these devices can do. They can also use their status as trusted network nodes to carry out “man in the middle” attacks, where they send malicious commands to connected devices.
One such attack causes devices to “bid down” to lower-quality network protocols, causing a degradation in the quality of their service. This could be a subtle yet highly damaging attack against corporate networks.
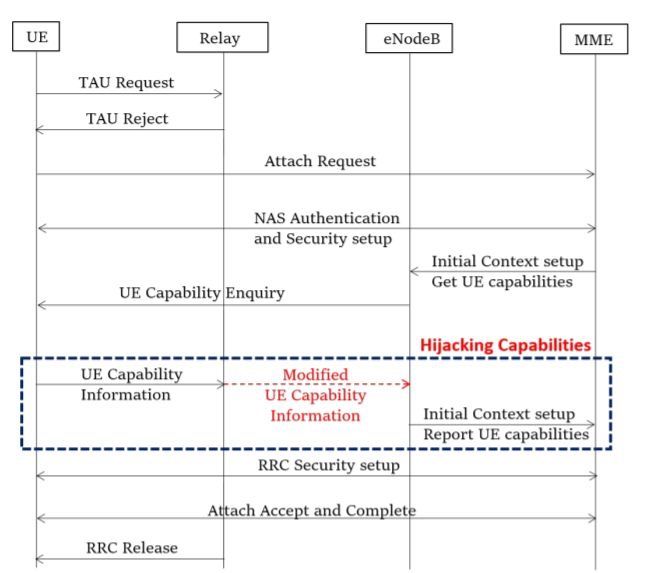
Due to the mobile network operators’ configuration or vendor implementations, the eNodeB requests UE’s radio access capabilities prior to RRC security setup. This allows a MitM (Man-in-the-Middle) to alter the UE Capability Information sent by the UE as seen in this figure.
The attack is persistent since capabilities are store at MME and reused by the eNodeB for every UE’s transaction.
