The Security Edge Protection Proxy (SEPP) is a proxy that sits at the perimeter of the PLMN network and enables secured communication between inter-PLMN network messages. It protects the home network and acts as a security gateway. Located at the edge of the network, it polices connections between the home network and the visited networks.
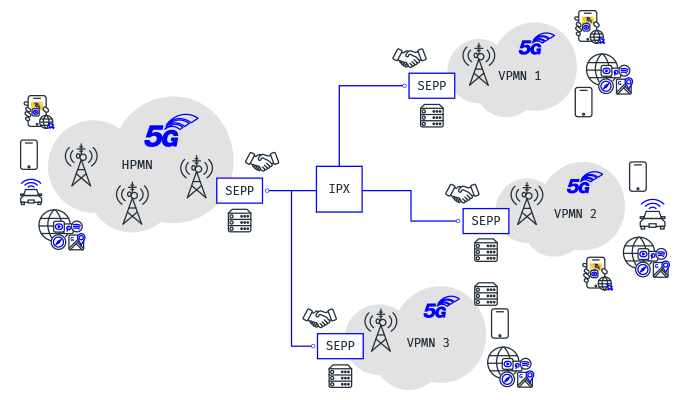
The SEPP supports the following functions:
- Provides authentication, confidentiality protection, and integration protection for interPLMN SBI signaling traffic between 5GC NF’s
- Implements N32 interface towards interconnect between vSEPP network elements:
- N32-C (Control Plane): N32-C is used to negotiate security capability between Local SEPP and Remote SEPP.
- N32-F (Forwarding Plane): which performs encryption/decryption on the messages to/from other PLMN’s SEPP based on negotiated capability.
- Provides topology hiding functionality by hiding the internal topology information of a PLMN from the external parties.
- Flexible routing control and resiliency features of SEPP allow the routing of inter-PLMN ingress messages to core network NF’s and routing of inter-PLMN egress messages to interconnect. SEPP also supports alternate routing in the case of an error message from the vSEPP or retry the request with the same provider in the case of a timeout.
- Supports configuration of roaming partner profiles & IPX provider profiles which is used for inter-PLMN routing of messages.
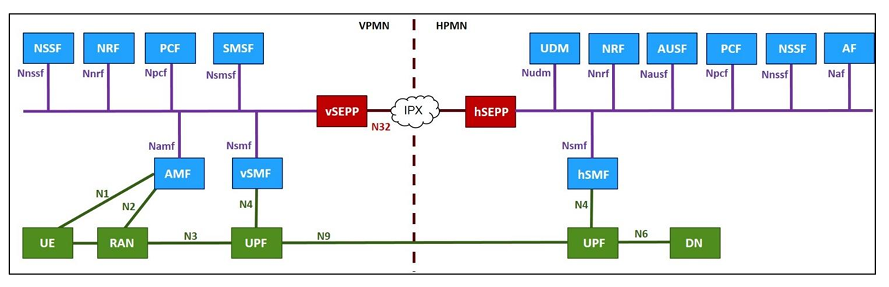
To protect messages that are sent over the N32 interface, SEPP:
- Receives all service layer messages from the Network Function (NF) and protects them before sending them out of the network on the N32 interface and
- Receives all messages on the N32 interface and forwards them to the appropriate Network Function after verifying security, where present.
Security Edge Protection Proxy (SEPP) Call Flow
- N32-C Flow:
The following is performed for N32-C flow:
This is the control plane of the N32 interface, When the SEPPs have mutually authenticated each other and when the negotiated security mechanism to use over N32 is Transport Layer Security, the SEPPs use the established TLS connection (N32-c connection) to negotiate the N32-specific associated security configuration parameters. Without Security Capability negotiation completed, SEPP can not process any data messages (N32-F) from the far end SEPP - N32-F Flow:
The following diagram illustrates a sample N32-F call flow between consumer & provider SEPP:
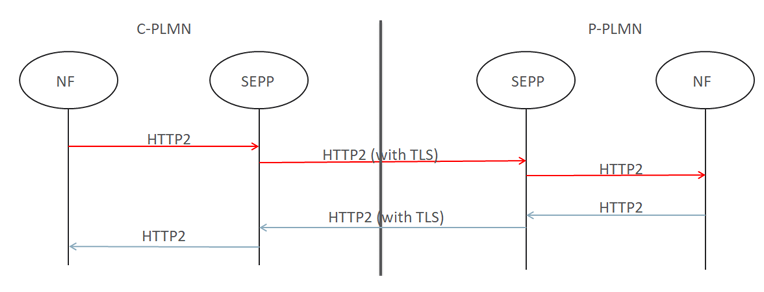
N32-F Flow
