Before starting to talk about IMSI Catcher, we need to understand what is the IMSI, its importance, and its structure. Based on this, we will discuss the IMSI catcher. So let’s GO 🙂
What is IMSI?
IMSI, International Mobile Subscriber Identity, is a unique static identity allocated to each subscriber in a mobile wireless system. IMSI was first introduced in the GSM standard, but the structure has remained the same for UMTS and LTE. The IMSI plays a crucial role in the network and UE authentication at the first initial attack from the UE.
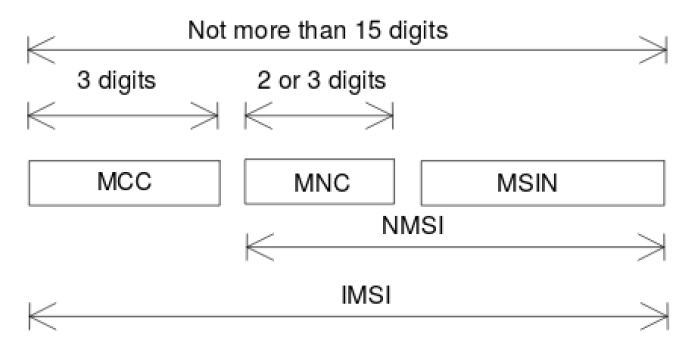
The IMSI is no more than 15 digits and is composed of MCC, MNC, and Mobile Subscriber Identification Number (MSIN). The MSIN uniquely identifies a subscriber within a PLMN while the MCC and the MNC identify the country and the network operator respectively.
Attackers are trying to get the IMSI of subscribers for differtent purposes like tracking.
How IMSI is protected?
Protecting subscribers’ identity is based on a serving network assigning a randomly generated Temporary Mobile Subscriber Identity (TMSI) to the mobile device at regular intervals. The long-term IMSI is used only as a fault recovery mechanism and when a TMSI has not yet been assigned. The recovery mechanism is needed to avoid lock-out of a mobile device when errors occur, e.g., when the serving network or the mobile device has lost the TMSI.
The mobile device falls back to using the IMSI whenever the serving network requests. This recovery mechanism is what IMSI-catchers exploit to obtain the IMSI from mobile devices. Hence, the current way of protecting privacy does not provide any protection against an active attacker on the air interface, claiming to be a legitimate network that has lost its temporary identity. Neither is there any protection against passive eavesdroppers who are present when IMSI requests are made.
So now we understand the confidentially of IMSI and how the mobile network operators are trying to protect it.
What is The IMSI Catcher?
An IMSI Catcher is essentially a device that acts as a false base station used to collect IMSIs from surrounding UEs. An IMSI Catcher is a device perceived as a real BS by UEs, used to perform several attacks in GSM, UMTS, and LTE. Although the IMSI Catcher appears as a real BS, it is not part of the infrastructure of a commercial PLMN. The main objective of the IMSI Catcher is to collect IMSIs from surrounding UEs.
IMSI catchers can be used to identify people. This matters due to the way that individuals throughout the world use and depend on their mobile phones.

Since IMSI permanently identifies a UE, this sort of identity disclosure is critical for user identity confidentiality. Consequently, by obtaining the IMSI of a UE, an attacker can track the movement of a subscriber over an extended period. Even more critical, the IMSI Catcher applied in GSM networks allows an adversary to perform MITM attacks. A hacker can intercept all messages between the UE and the serving network by exploiting the vulnerability that GSM AKA does not support mutual authentication.
IMSI Catchers have existed for a long period, and the first IMSI Catcher was commercially launched by the German company Rohde & Schwarz in 1996. The hacker The student can build an IMSI Catcher based on the open-source platform OpenAirInterface.
In the past, active IMSI-catchers such as StingRay were expensive (in the range of $68,000-$134,000) and sold only to law enforcement and government officials. However, advances in low-cost software-defined radio made active IMSIcatchers relatively cheap and accessible. In 2010, Chris Paget demonstrated that it is possible to build a homemade active IMSI catcher for about $1,500 using a software-defined radio, two directional antennas, and a laptop running OpenBTS and Asterisk.
IMSI catchers Capabilities
- Monitoring and intercepting communications, including phone calls and text messages.
- Monitoring and intercepting communications data.
- They are forcing all mobile phones within range to transmit their IMSI and IMEI data, which can identify people.
- Enabling the location tracking of mobile phones (and therefore their users).
- Indiscriminately monitoring and collecting people’s data (including those of nonsuspects).
IMSI Catching Attack Types
The IMSI catching attack can be done passively or actively.
- A passive IMSI catcher eavesdrops on the wireless traffic in its neighborhood and collects all IMSIs captured.
The coverage area of the IMSI-catcher is dependent on receiver/antenna technical properties. If it is possible to build an antenna of similar gain and at a similar height as an authentic base station, e.g., on a building rooftop, the coverage area could be roughly the same as that of a normal cell in the network. Listening over a large area can be done using a mobile setup or a network of receiving antennas. The presence of receiving antennas is difficult to detect. However, the passive approach is slow since an attacker has to wait for a mobile device to transmit its IMSI spontaneously, which is an uncommon event in most locations (exceptions are, e.g., airports). - A faster, active way to catch IMSIs is to set up a ”fake” base station which acts as a preferred base station in terms of signal strength. Mobile devices typically prefer base stations emitting the strongest signal. This fake base station can then be used to send an Identity Request message to all mobile devices in the area, which will respond with their IMSIs since they assume that they are connected to a real network that has lost access to the TMSI. In this way, IMSIs of all mobile devices in the area can typically be captured rapidly.
In the next article, I will discuss in more detail the IMSI protection from 2G to 5G and how 5G adds more privacy to protect the IMSI 🙂
