5G Timeline and Standardization
During preparation, it was decided to split Phase 1 into two parts.
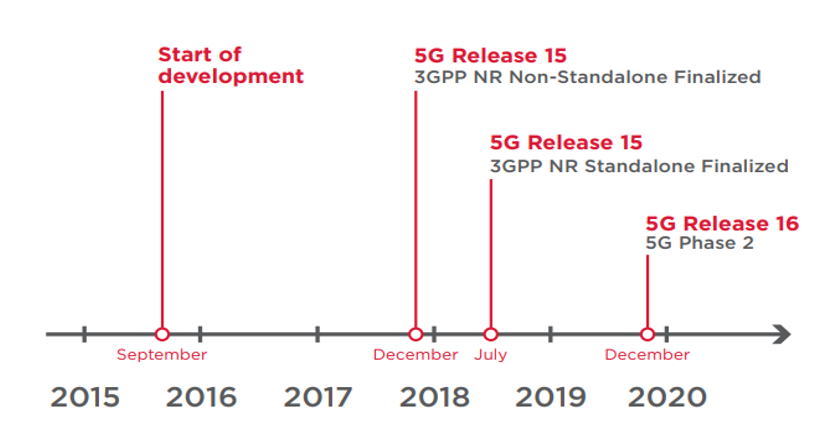
In December 2017, standardization of the non-autonomous, or Non-Standalone, architecture for 5G New Radio (NR) was completed. This first official set of 5G standards defines the wireless air interface for interworking with existing LTE-based networks. This has allowed operators to combine 4G LTE networks with 5G NR, improving the latency and bandwidth of user data transmission.
In July 2018, the first stage of standardization for 5G Phase 1 was completed. As part of 3GPP Release 15, NR Standalone architecture specifications were released, indicating how the proposed 5G radio network will work with a 5G network core.
5G NSA Vs. 5G SA Security
According to 3GPP Release 15 for 5G, which came out in summer 2018, the first wave of 5G networks and devices is classified as 5G Non-Standalone (NSA). 5G radios will be supported by the existing 4G infrastructure. In other words, devices will connect to 5G frequencies for data transmission when needing greater bandwidth and lower latency (such as for communication between smart cars), or to reduce power draw on IoT-enabled devices, but will still rely on 4G and even 2G/3G networks for voice calls and SMS messaging. So, at least during the transition period, future 5G networks will inherit all the vulnerabilities of previous generations.
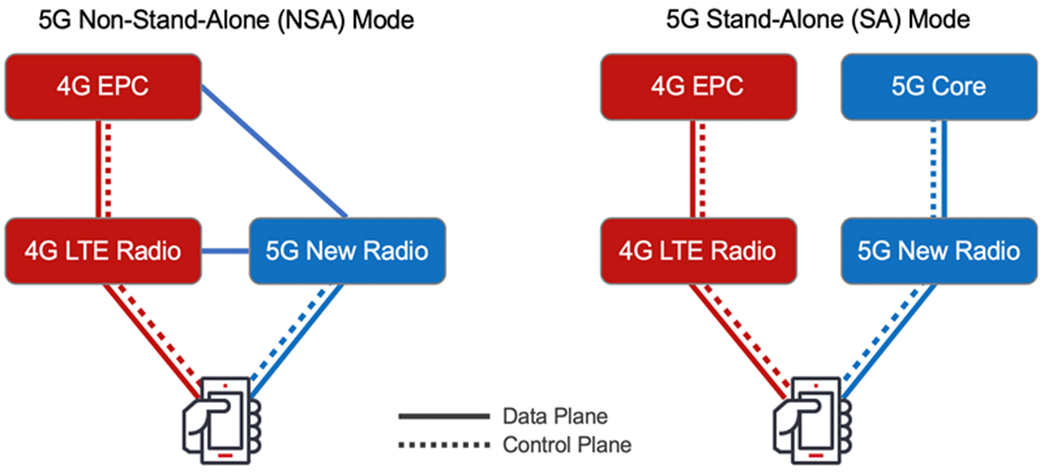
5G Standalone networks may add new types of security flaws because the entire packet core and additional services will depend on virtualization. Technologies such as NFV and SDN will make deployment simpler, faster, and more flexible. But replacing dedicated hardware with software-defined systems (some of them based on open-source code) may prove a double-edged sword that makes mobile networks more vulnerable to attacks.
“5G New Services, Architectures and Technologies Will Bring Security Challenges”
Security architecture, authentication, security context, and key management, radio access network (RAN) security, security within NG-UE, authorization, subscription privacy, network slicing security, relay security, network domain security, security visibility, and configurability, credential provisioning, interworking, and migration, small data, broadcast/multicast security, management security, and cryptographic algorithms.
Key assets of 5G networks include users’ personal data and communication data, hardware and software assets of wireless and core networks, computing resource assets, as well as accounts, passwords, logs, configurations, and charging data records (CDRs) operated and maintained by operators.
In general, most threats and challenges faced by 5G security are the same as those faced by 4G security. However, the security challenges brought by new services, architectures, and technologies to 5G networks need to be considered.
- In terms of new services, consideration must be given to access authentication for third-party slicing service providers
- 5G cloud architecture.
With 5G wireless networks, over 7 trillion wireless devices serving over 7 billion people will be interconnected, ushering a new era of security threats, and a greater focus on privacy.
Next article, we’ll discuss what is the difference between 4G Security Architecture and 5G Security Architecture.
Source: GSMA, Huawei, Ericsson, NEC
