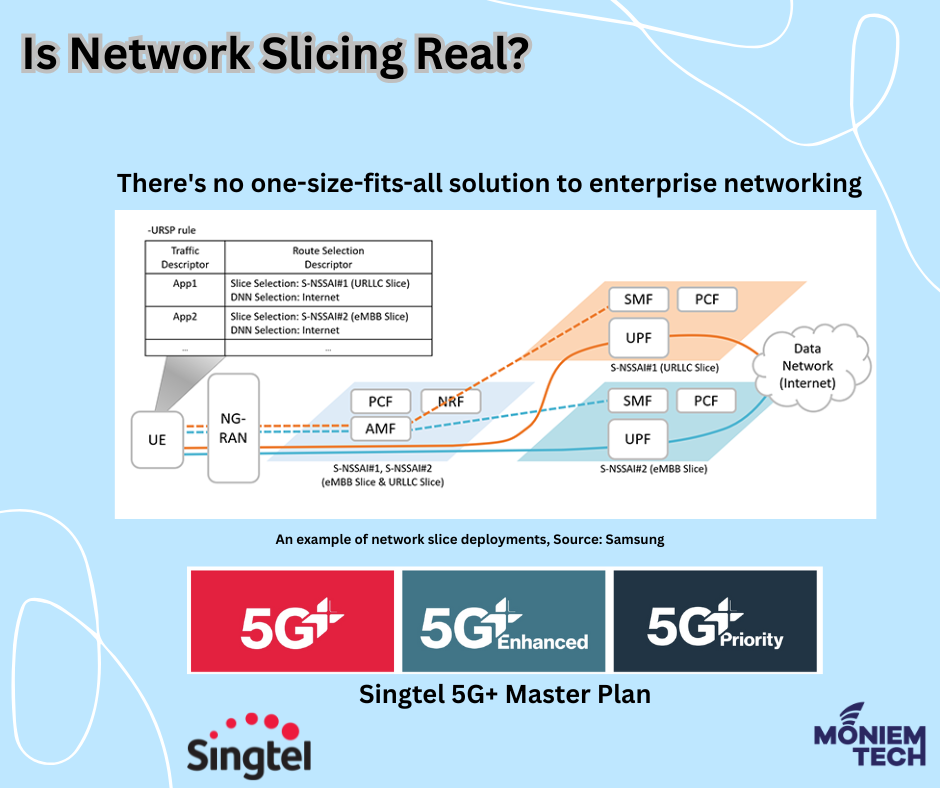
Network Slicing is essentially the ability to divide your network into individual use cases, each tailored to provide specialised services. Traditionally, in 4G, the APN (Access Point Name) was probably the earliest form of network slicing in a mobile network, allowing operators to divide their networks according to service requirements. Accurate 5G network slicing, as […]
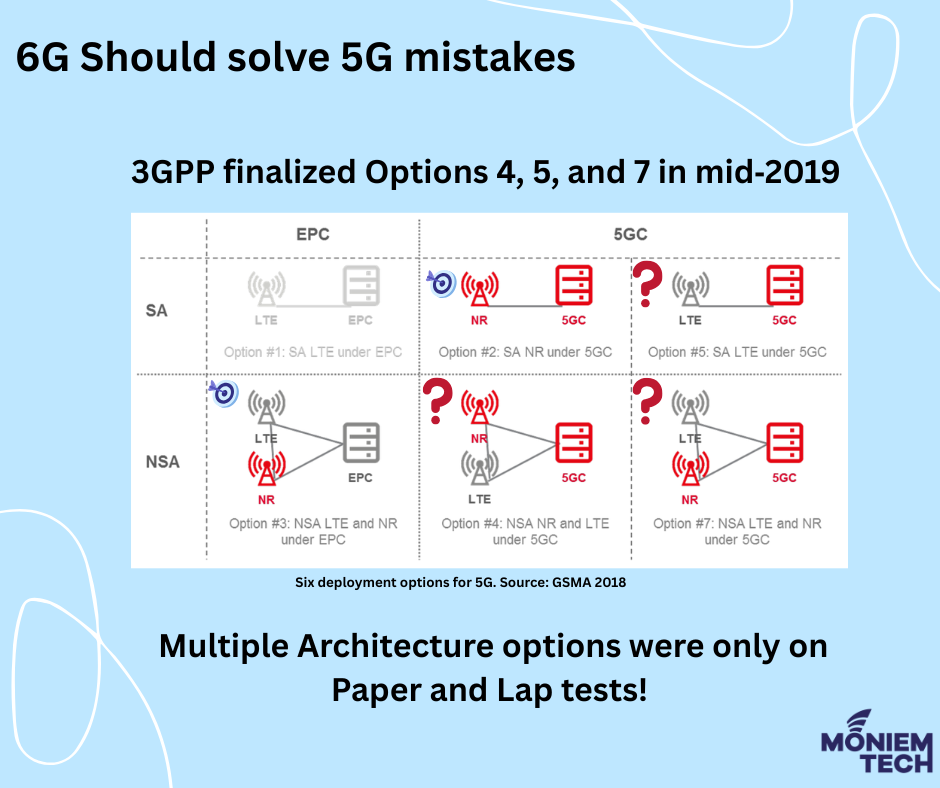
For the introduction of 5G, 3GPP has specified five possible configurations, or ‘options’, for connecting to an EPC or a new 5G core network (six if the current 4G system is included). The features that distinguish each Option are: Use of Dual Connectivity; Radio Access Technology acting as master node Core Network used. The Options […]
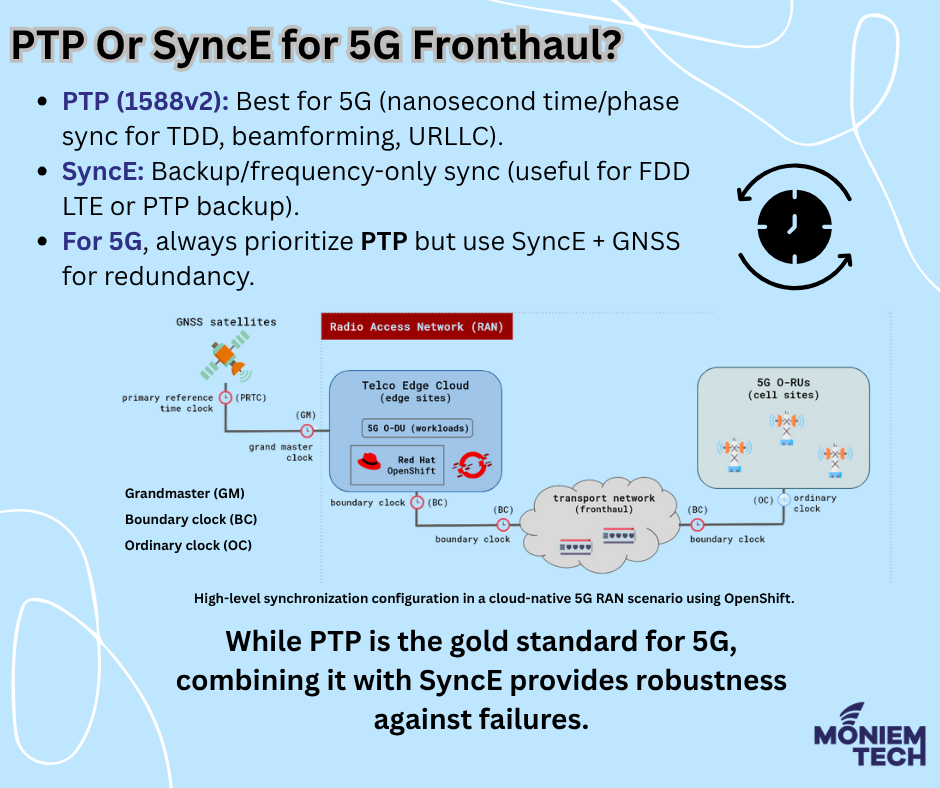
Synchronization in 5G ensures precise timing and coordination across the network, enabling key technologies like TDD, beamforming, and ultra-low latency. 5G TDD networks utilise the same frequency for both uplink (UL) and downlink (DL), with time slots separating them. If base stations are out of sync, UL/DL transmissions collide, resulting in interference and dropped connections. […]
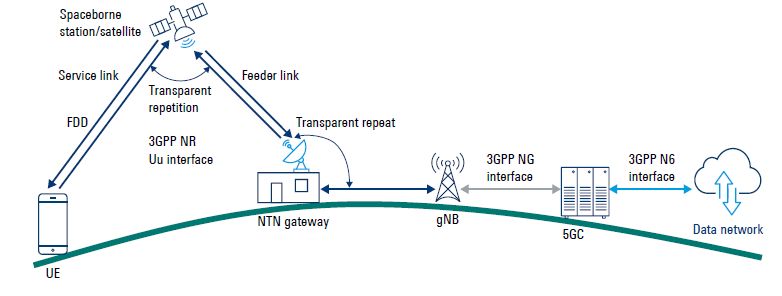
The 5G Non-Terrestrial Network (NTN) integrates satellite and airborne platforms with terrestrial 5G networks to provide ubiquitous coverage. The Next-Generation Radio Access Network (NG-RAN) architecture in 5G NTN can be designed to be transparent (i.e., with minimal on-board processing) to reduce payload complexity while ensuring seamless interoperability with terrestrial 5G systems. A transparent NTN payload acts as […]
Interworking security between 5G and EPC involves managing security contexts during mobility between the two systems. This ensures that the UE can maintain secure connections regardless of the access technology used. The UE can operate in Single or Dual Registration mode, maintaining separate security contexts for each system. During mobility from EPS to […]
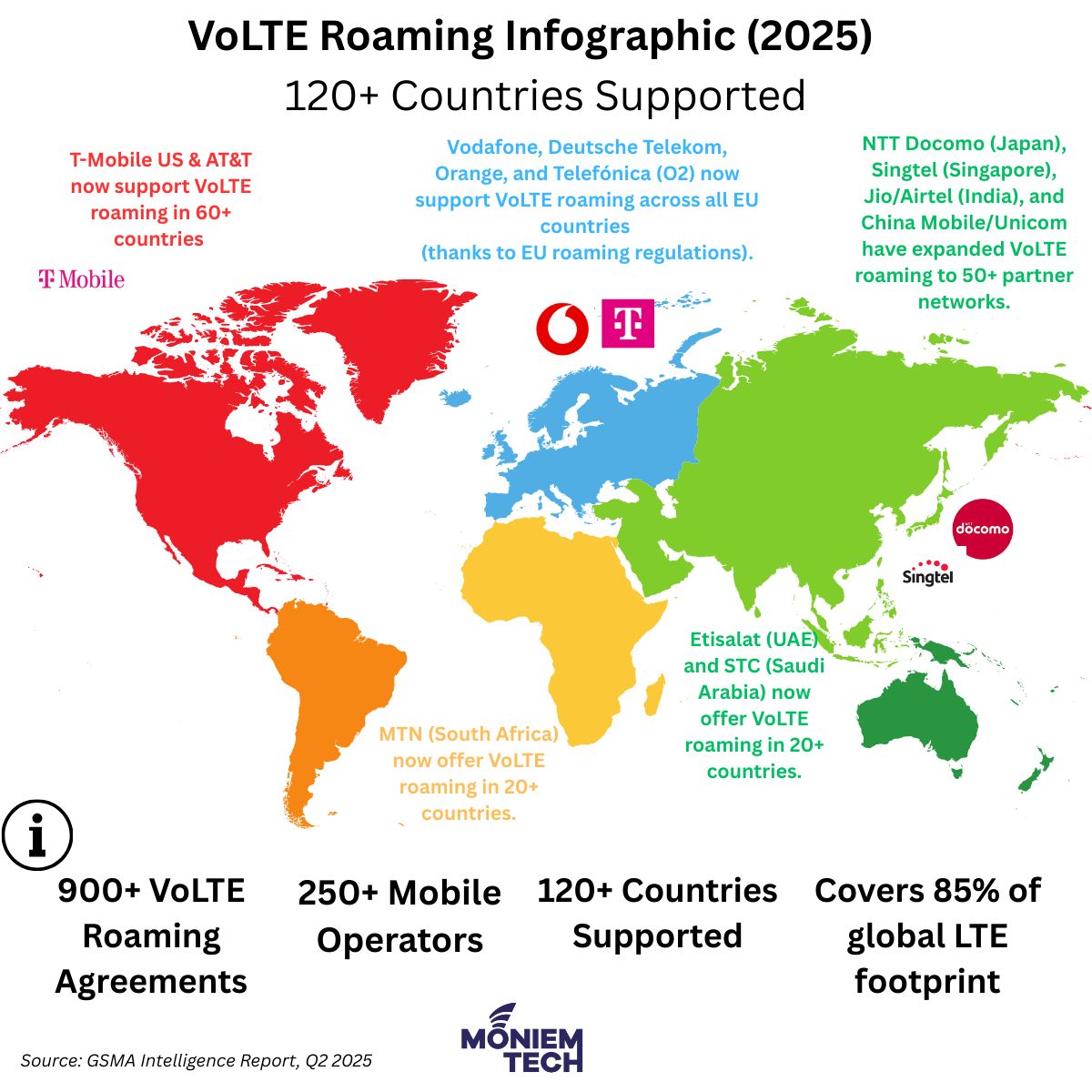
As of April 2025, the global landscape of Voice over LTE (VoLTE) roaming agreements has expanded significantly, reflecting the industry’s shift towards all-IP voice services and decommissioning legacy 2G/3G networks. Global VoLTE Roaming Agreements According to the GSMA, over 900 VoLTE roaming agreements have been established worldwide. These agreements involve more than 250 mobile network operators across approximately […]
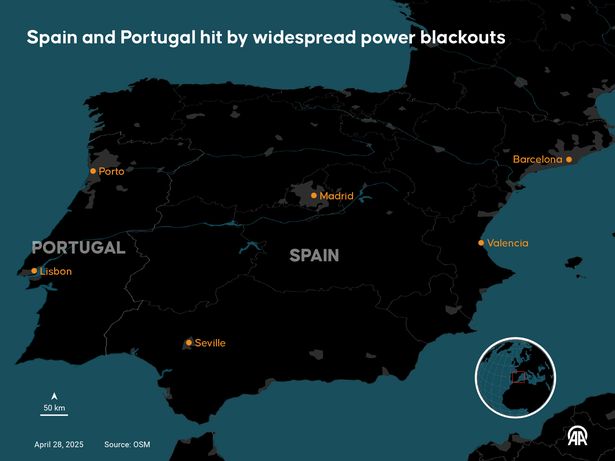
The blackout, which began around midday, disrupted essential infrastructure, including mobile networks, internet services, and emergency communication systems. In both Spain and Portugal, users experienced difficulties with voice calls, and data services were only partially functional. This disruption affected not just everyday communication but also critical services like hashtag emergency calls and public safety communications. In […]
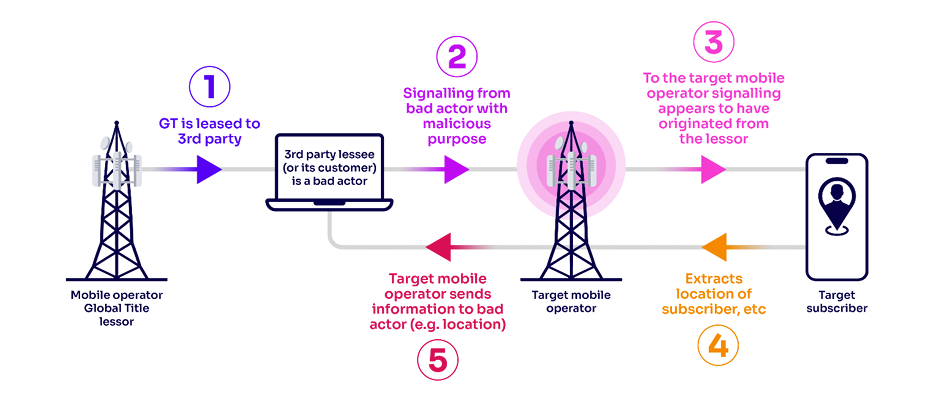
I wrote an article before about ” What is GT (Global Title)? Why Do We Need It?” What is Global Title Leasing? GT leasing is the practice of a mobile operator entering into a commercial arrangement to allow another operator to use one or more of its GTS. Lessees obtain access to the global SS7 […]

Last weekend, by coincidence, I found a fraud story related to the Telecom domain called “Spoofing CLI” or “Calling Line Identification (CLI) spoofing.” which is a technique used in mobile network fraud where the caller purposefully fakes the phone number or the caller ID information that appears on the recipient’s device. CLI is the phone […]

The SS7 network was once considered an environment that controls users’ access to network-based content and services, allowing licensed mobile operators to access customer data. However, many unlicensed entities currently have access to the SS7 network, taking advantage of the low security of this protocol. Consequently, more businesses and individuals with direct access to the […]

Many types of firewalls are often categorized by system protection, form factor, network placement, and data filtering method. Regarding 5G, Firewalls protect different network layers — especially in the Service-Based Architecture (SBA) of 5G Core. This includes: Perimeter Firewall (Traditional Role) It protects 5G infrastructure from external threats and is deployed at the edge of […]
