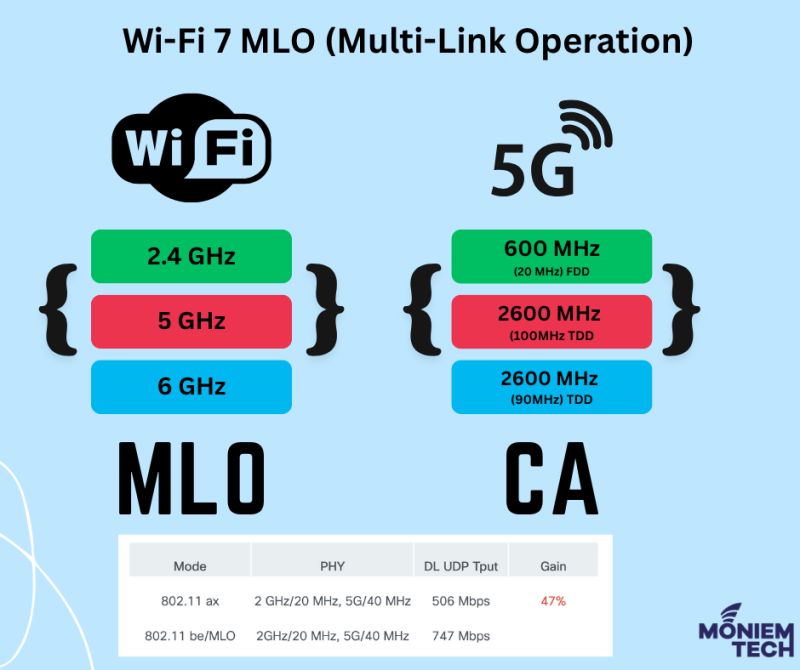
Existing Wi-Fi 6 devices support multiband operations across the 2.4 GHz, 5 GHz, and 6 GHz bands. However, these operations are independent, lacking coordination and significantly reduce efficiency. To address […]
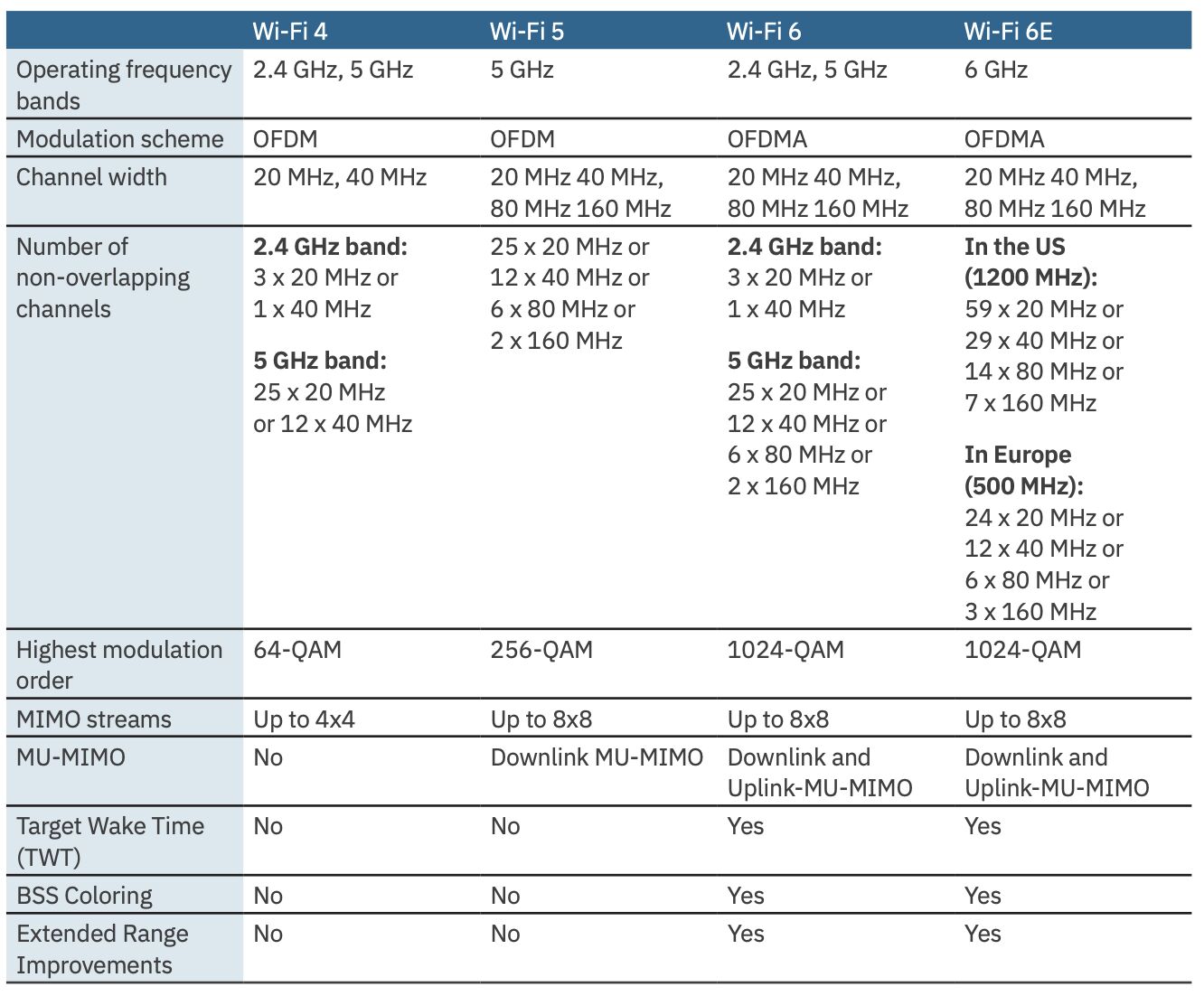
Wi-Fi remains the default solution for indoor connectivity, handling the majority of data traffic across smartphones, tablets, and IoT devices. According to the UK telecoms regulator Ofcom, in its 2022 […]
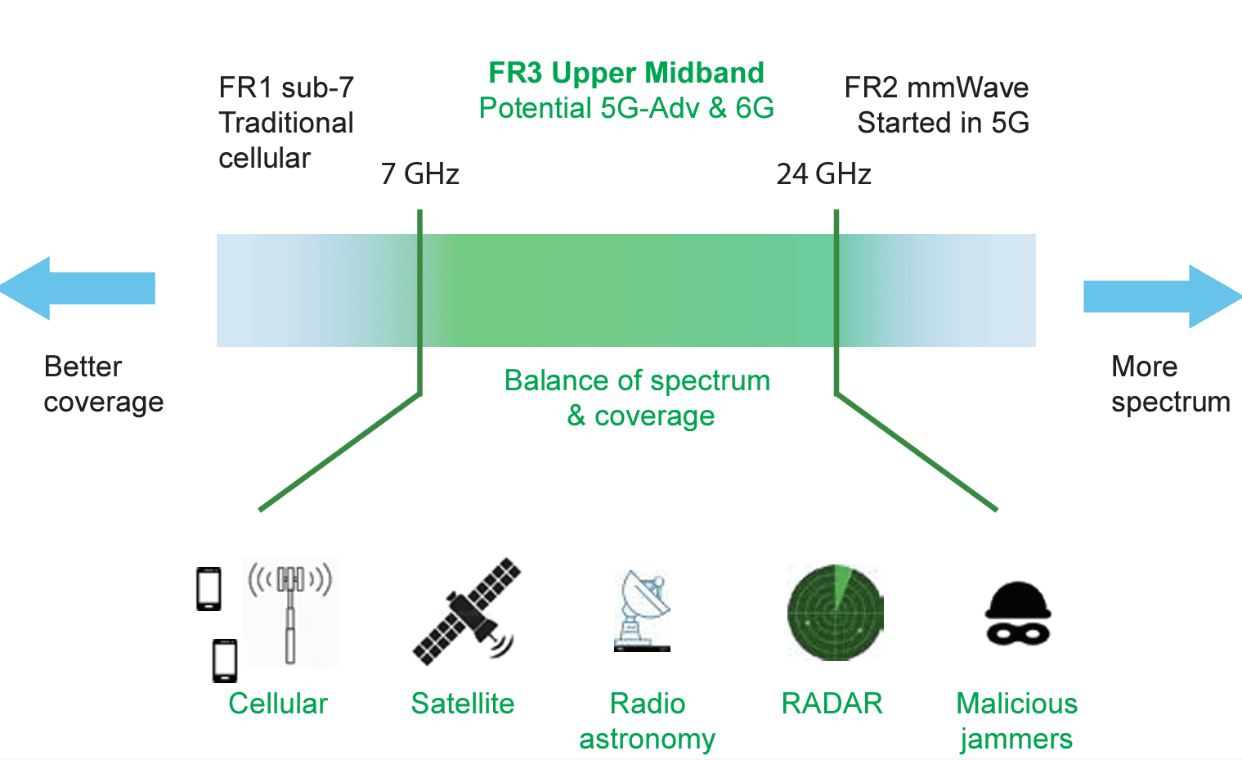
Recently, I have read an interesting white paper from Anritsu, which covered trends in wireless frequency band allocation for 5G-A and 6G. The most recent WRC was held in Dubai, […]

If you’re living in the UAE, you’ve probably noticed the new billboards across the streets promoting the latest evolution of 5G technology. Etisalat is calling it 5.5G (5G-Advanced) while DU […]

mmWave offers the fastest 5G speeds available today; however, its use cases are currently limited. With its extremely short range and poor penetration through obstacles, mmWave mainly makes sense in […]
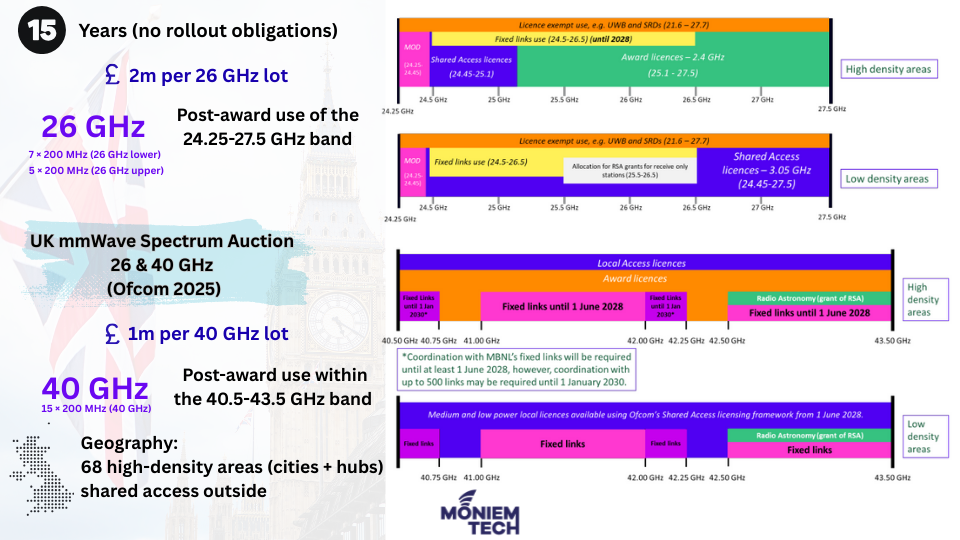
Ofcom is auctioning a total of 5.4 GHz of mmWave spectrum across the 26 GHz and 40 GHz bands. This marks a significant milestone for 5G evolution in the UK […]
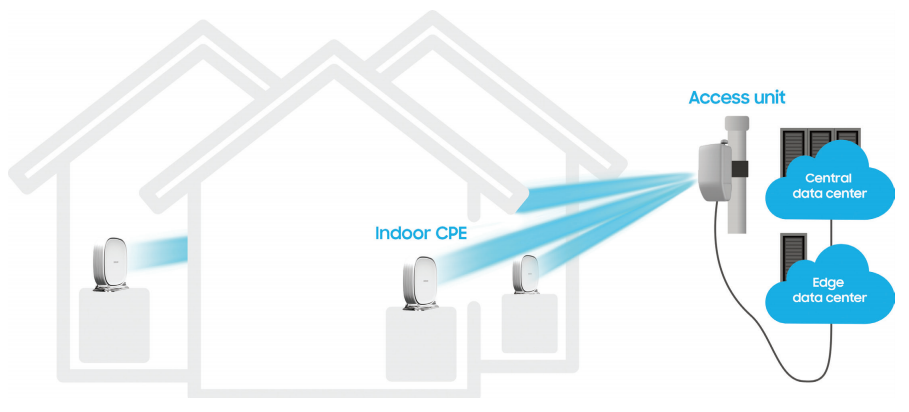
5G FWA isn’t just a “nice-to-have” – it’s the future of home connectivity. The latest data from CTIA shows a clear trend: 5G FWA is driving nearly all new broadband growth […]
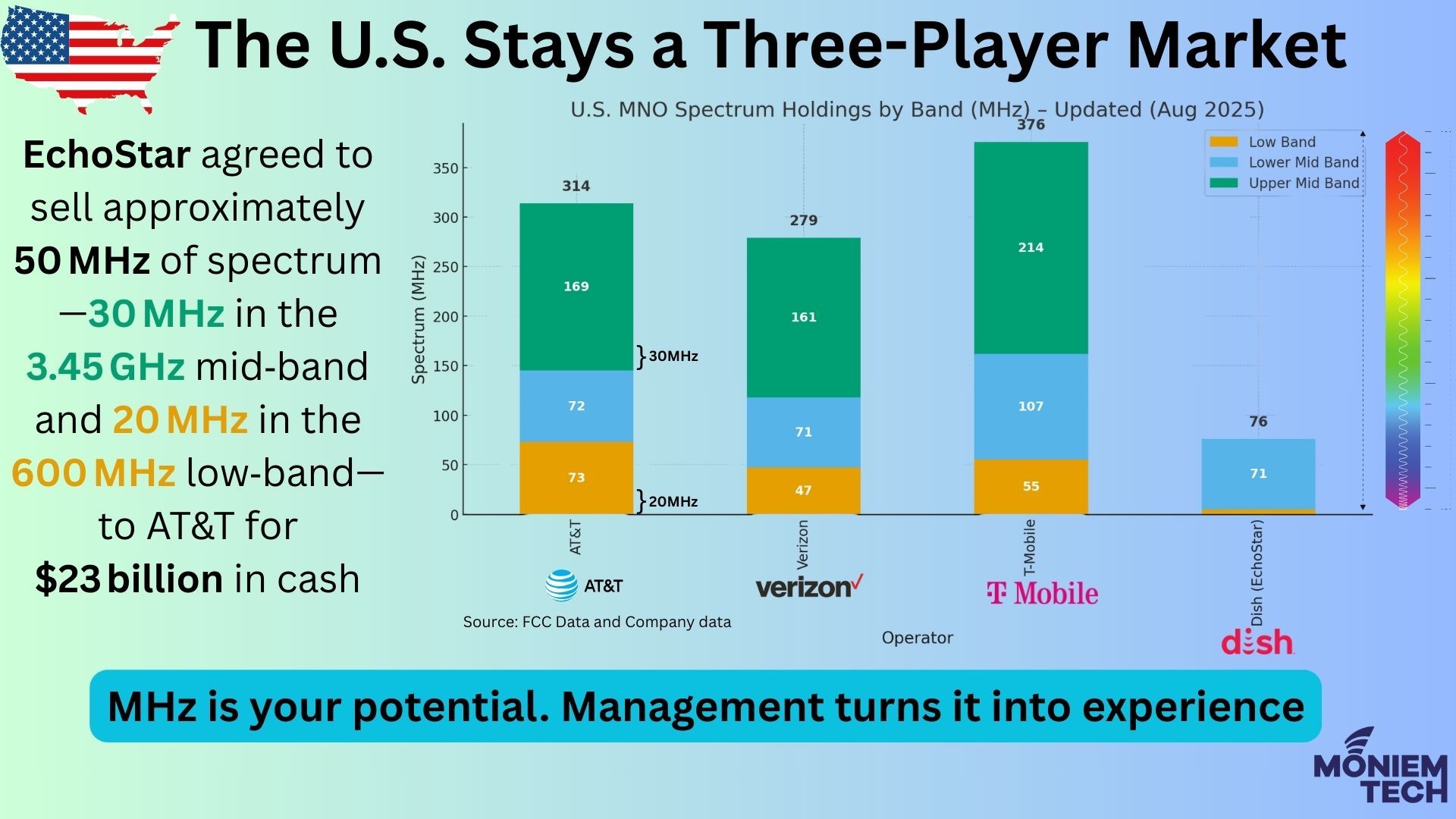
For many years, policymakers, regulators, and industry observers maintained expectations for a fourth national wireless carrier to contend with AT&T, Verizon, and T-Mobile. This anticipation primarily relied on DISH Network, which […]
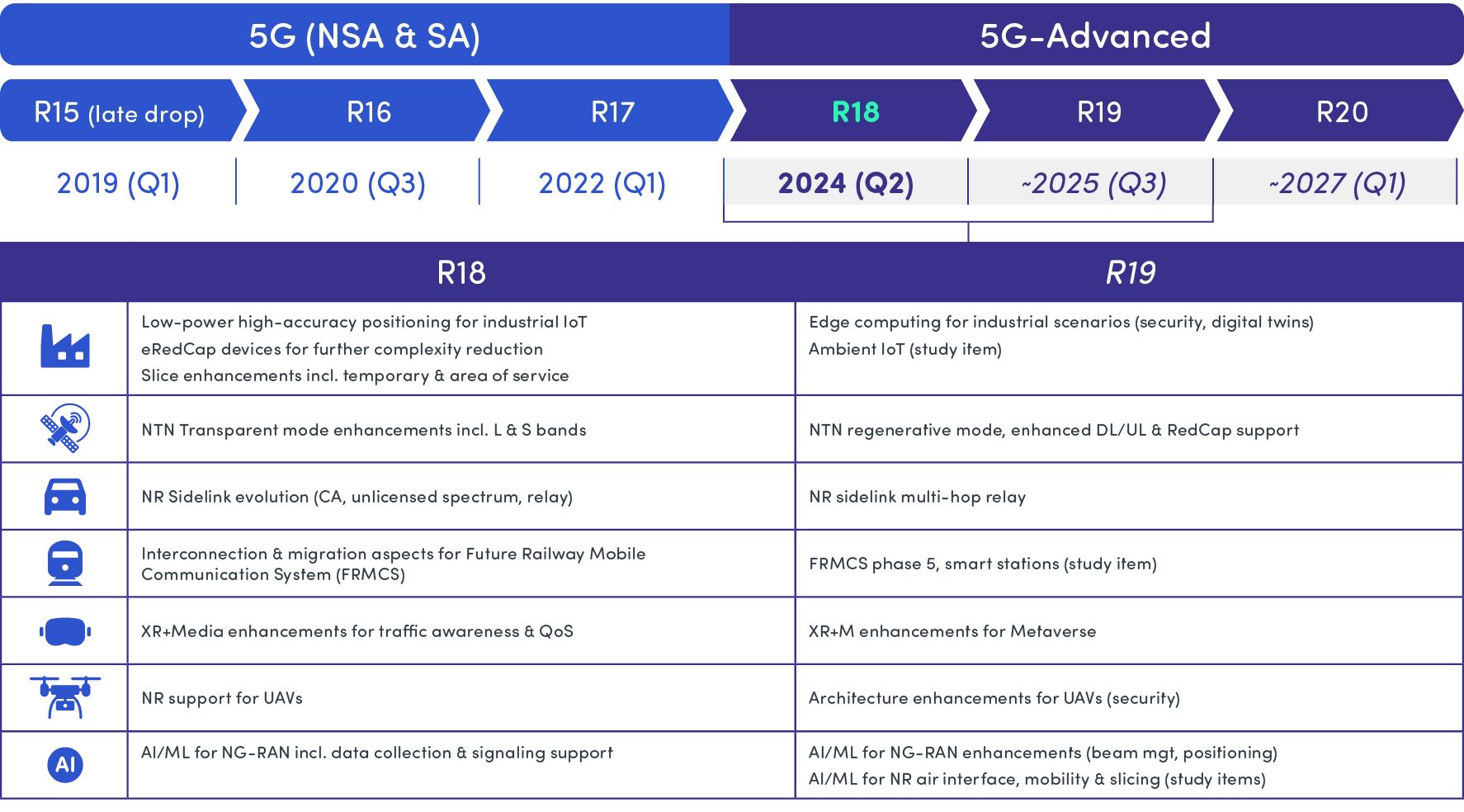
The recent Spirent article rightly highlights the potential of 5G-Advanced (5G-A) and the role of the 5G Core in enabling monetization. However, 5G-A should be seen primarily as a future-oriented […]
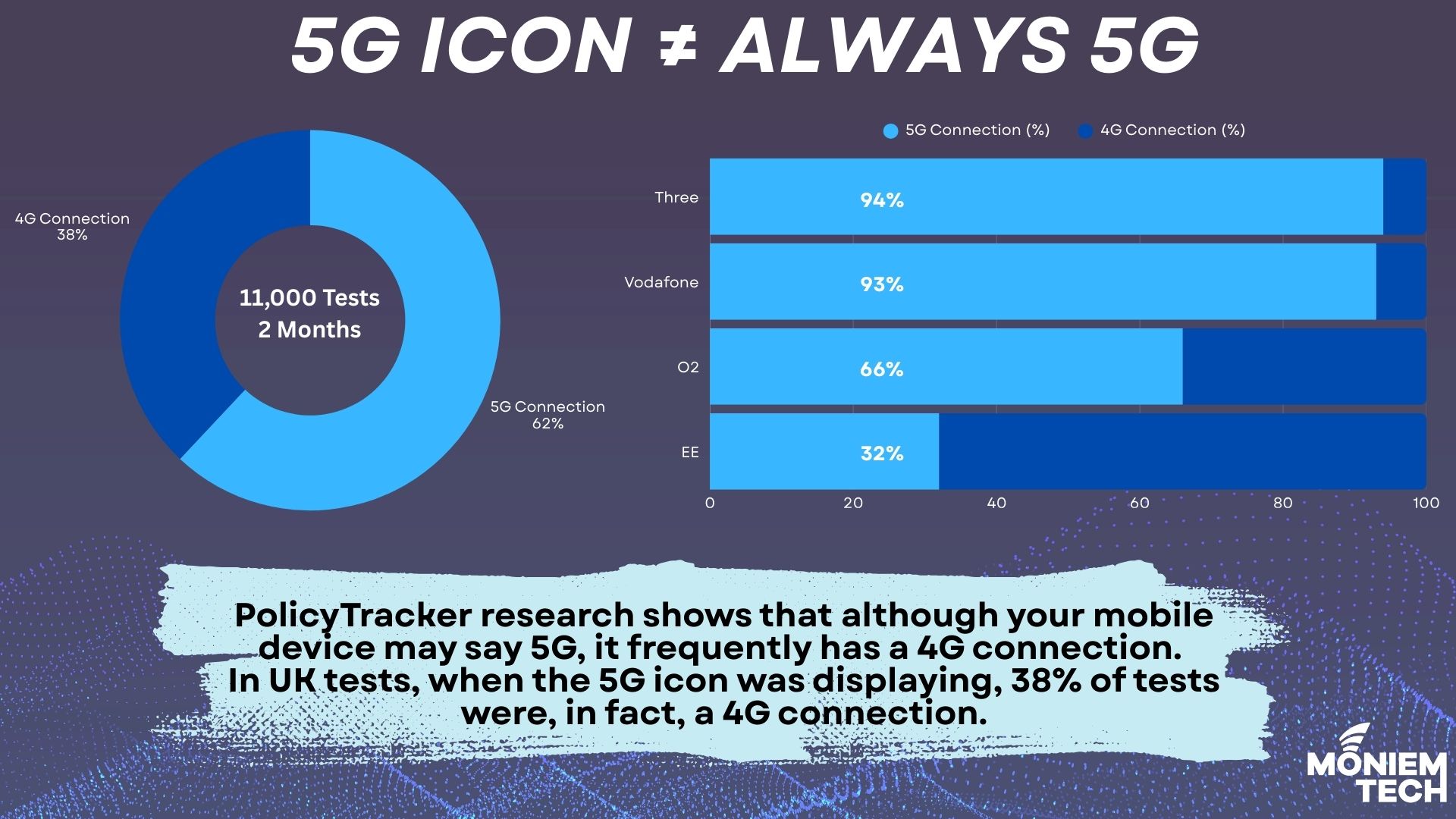
The question is: Actual 5G or Icon-only 5G. A study based on the mobile app SignalTracker shows that nearly 40% of 5G connections are actually 4G, as per PolicyTracker. Actual […]
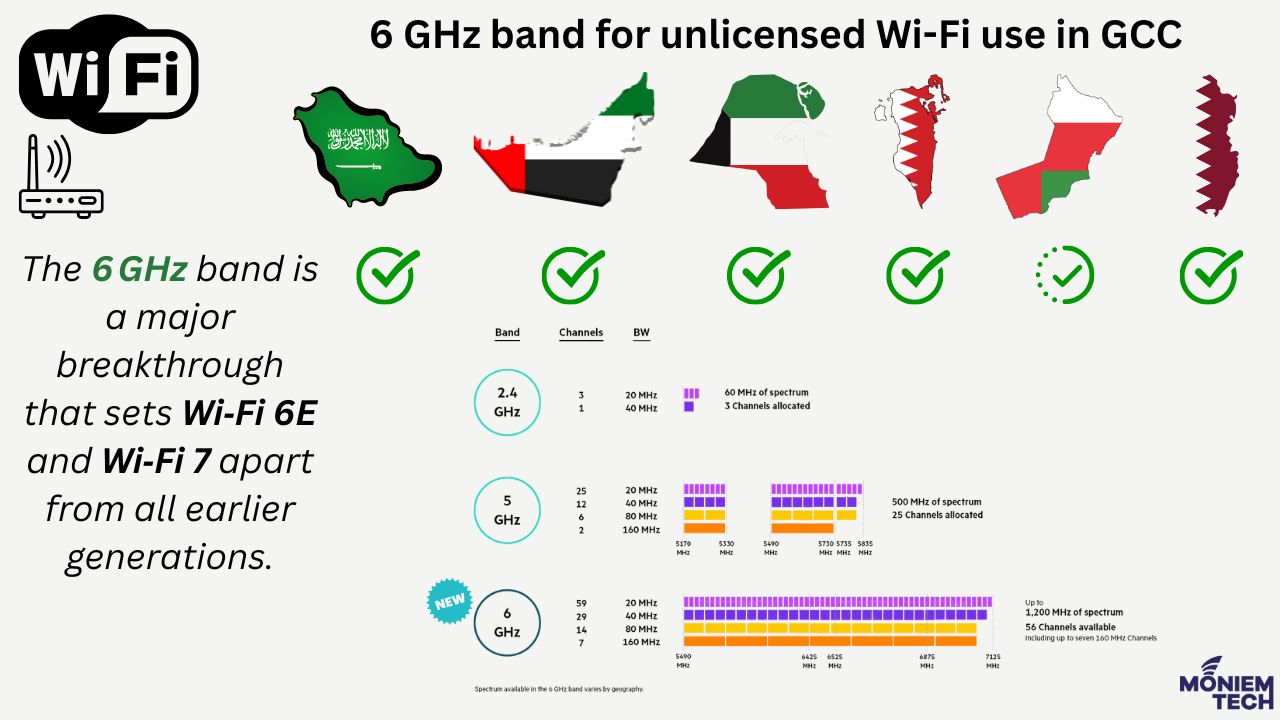
Wi-Fi is a key resource in the world communications ecosystem. Up to 90% of all mobile device traffic is carried on Wi-Fi. The 6 GHz band is a breakthrough that sets […]
