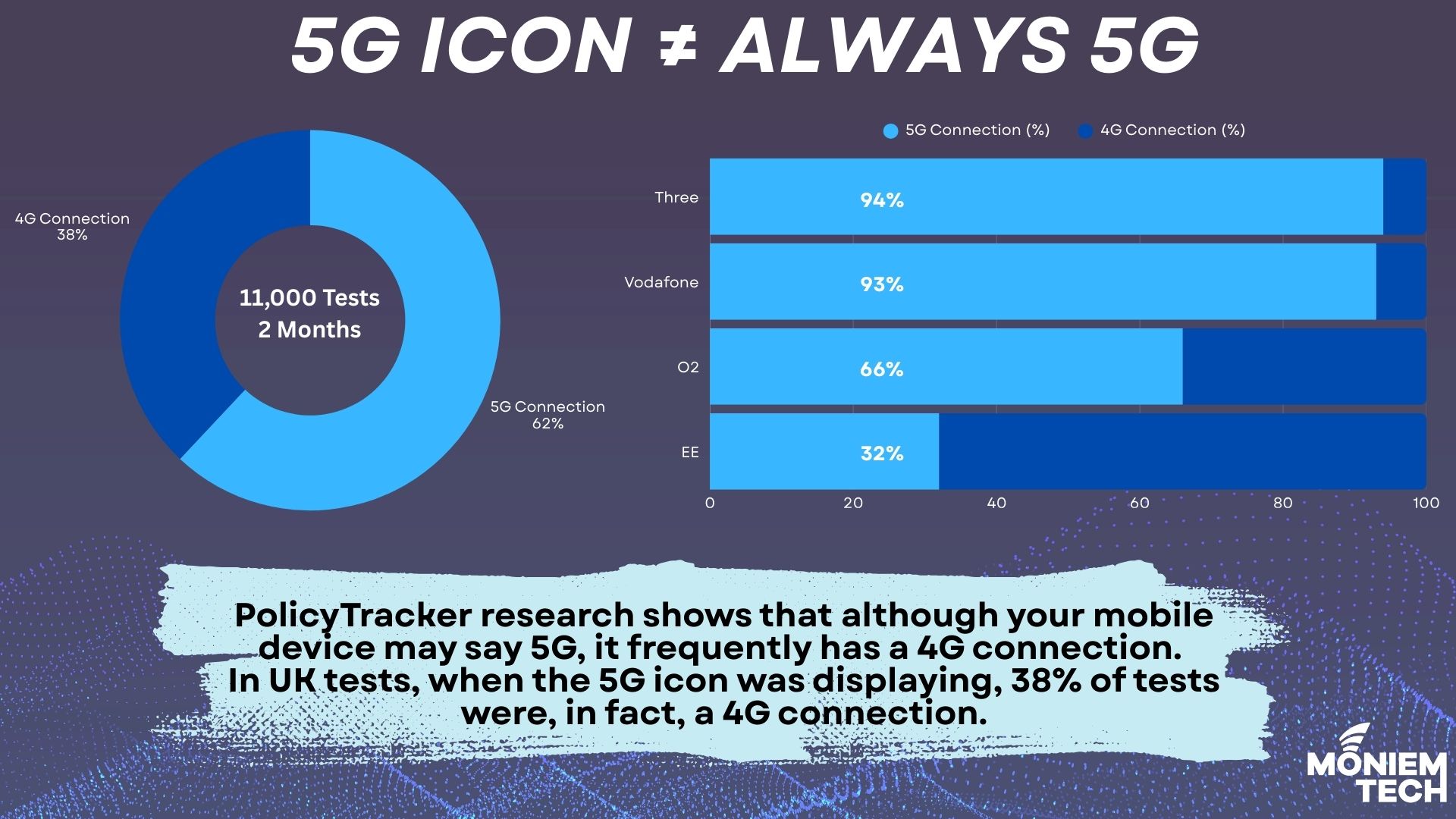
The question is: Actual 5G or Icon-only 5G. A study based on the mobile app SignalTracker shows that nearly 40% of 5G connections are actually 4G, as per PolicyTracker. Actual […]
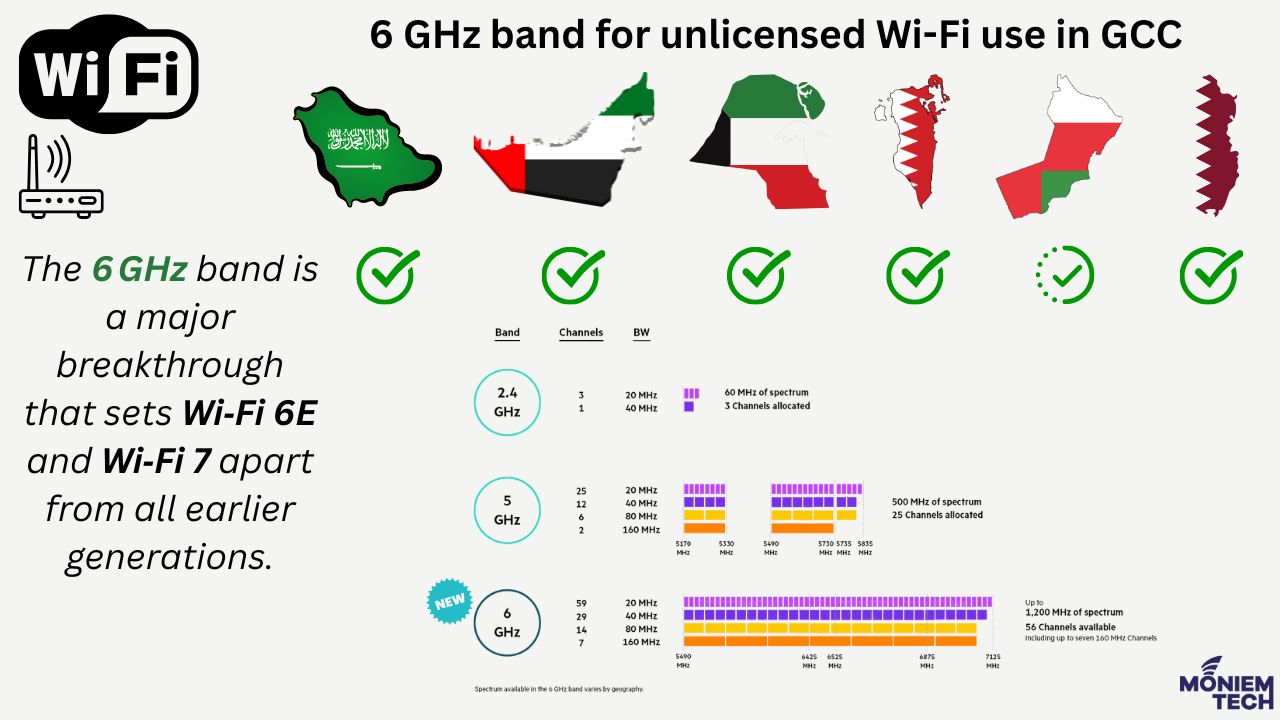
Wi-Fi is a key resource in the world communications ecosystem. Up to 90% of all mobile device traffic is carried on Wi-Fi. The 6 GHz band is a breakthrough that sets […]
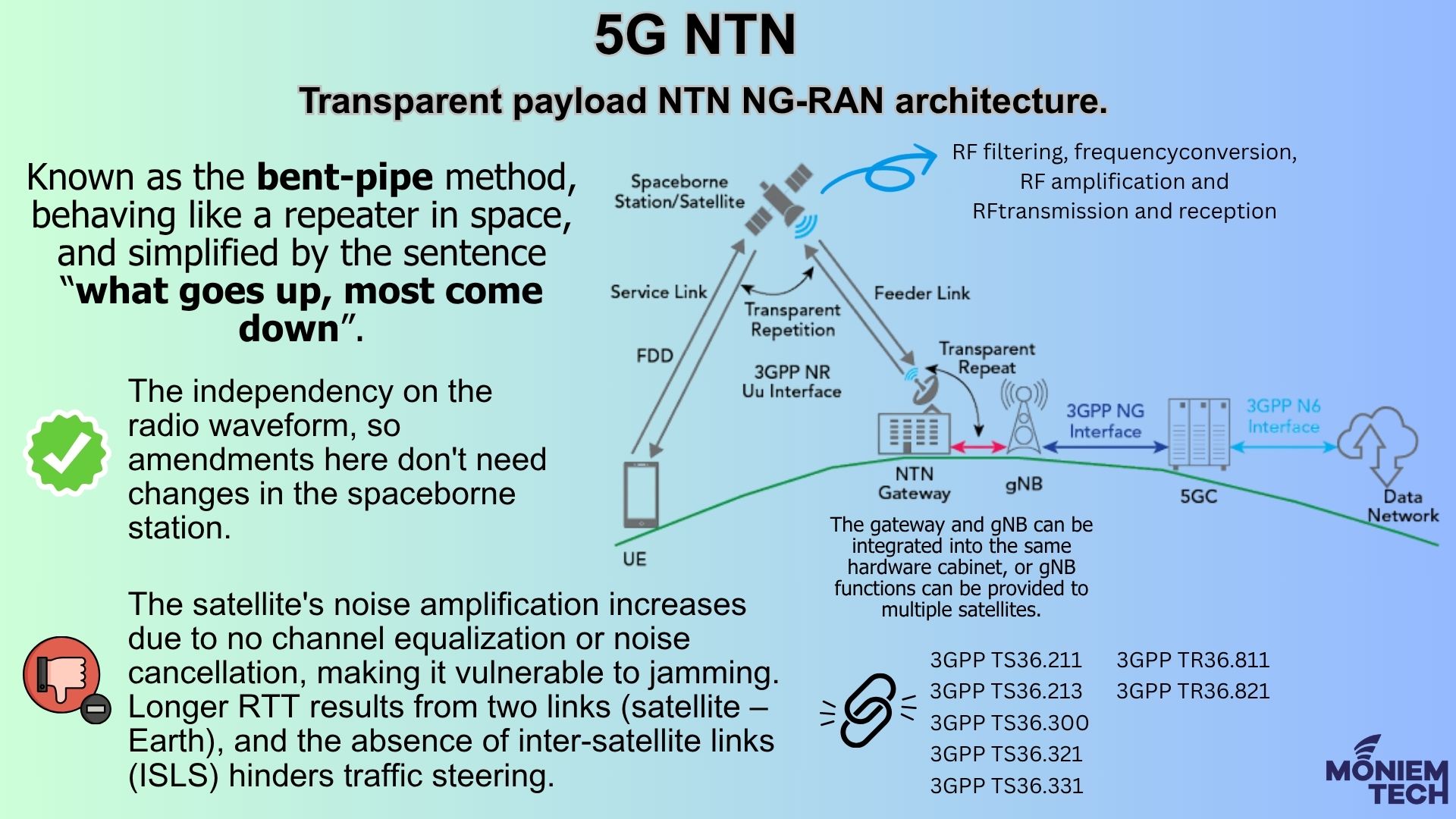
When discussing 5G NTN, it’s important to understand what NTN is, how it functions, and the purpose of Transparent Architecture. What is 5G NTN? 5G NTN refers to the integration […]
Before the advent of Rel.17, IoT deployments were plagued by connectivity challenges, especially in remote and rural areas. Terrestrial networks often fall short in providing reliable coverage, resulting in data […]

Imagine being able to download every HD video on Netflix in just one second… Now, with Japan, we can say yes. Japan’s National Institute of Information and Communications Technology (NICT) achieved […]

The upcoming Android 16 release introduces a critical new security feature: Network Notification Warnings This enhancement is designed to alert users in real time when their mobile devices are exposed […]
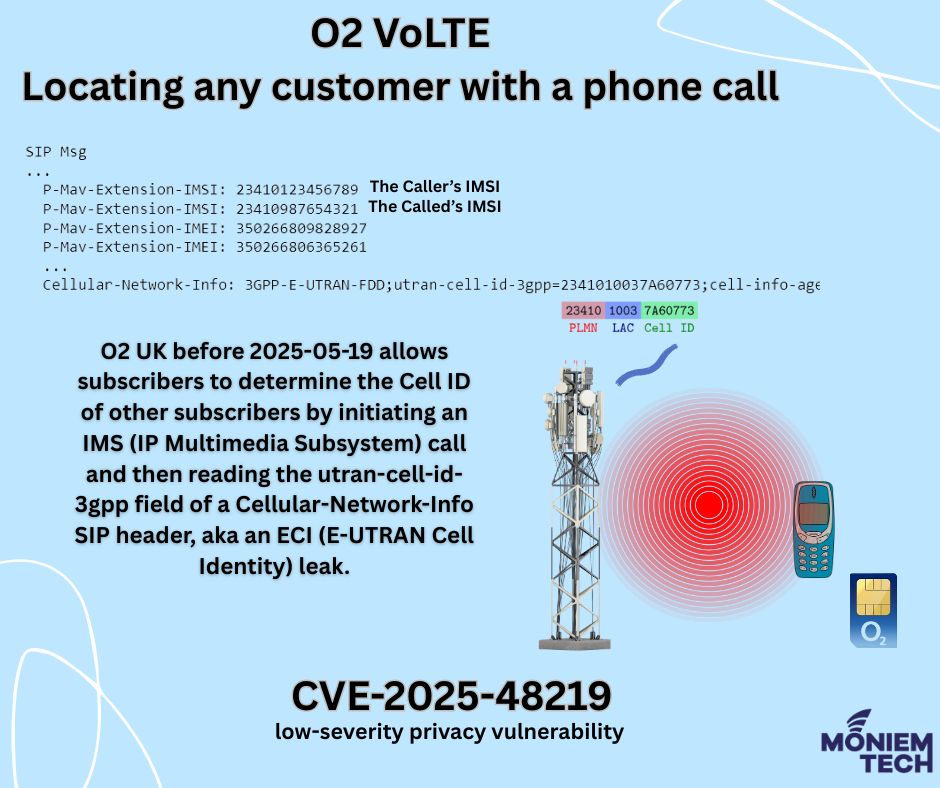
Vulnerability Details: CVE-2024-53026. It is a vulnerability affecting O2 UK’s VoLTE/IMS service, disclosed in mid-May 2025. Rated Low, with a CVSS v3 score of 3.5. It has a limited impact on confidentiality […]
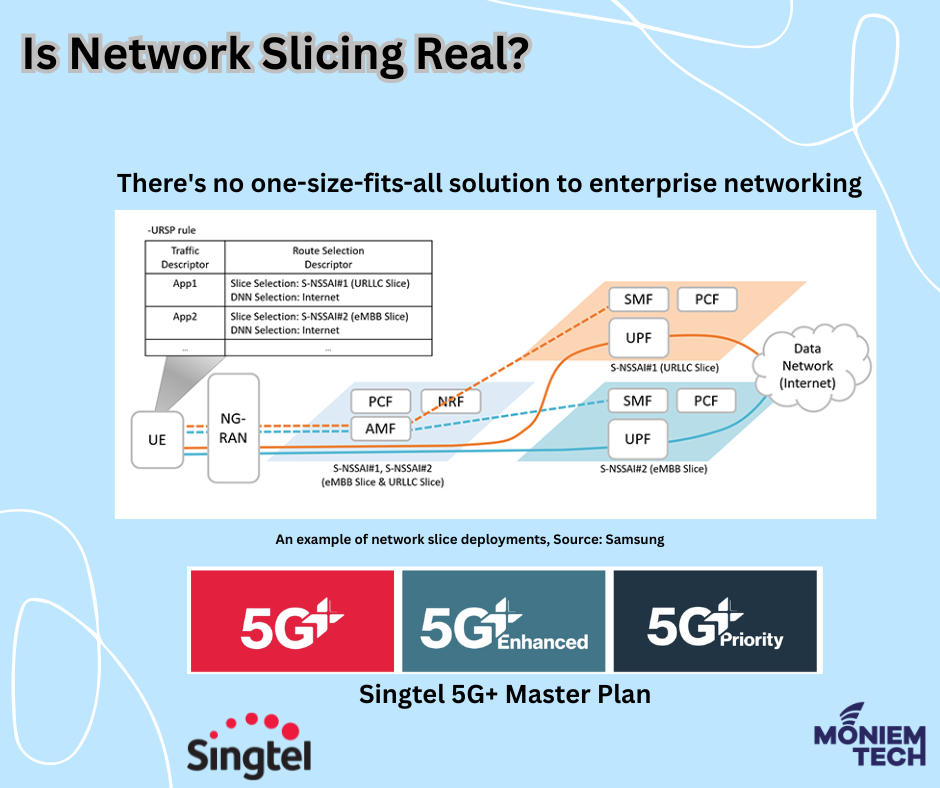
Network Slicing is essentially the ability to divide your network into individual use cases, each tailored to provide specialised services. Traditionally, in 4G, the APN (Access Point Name) was probably […]
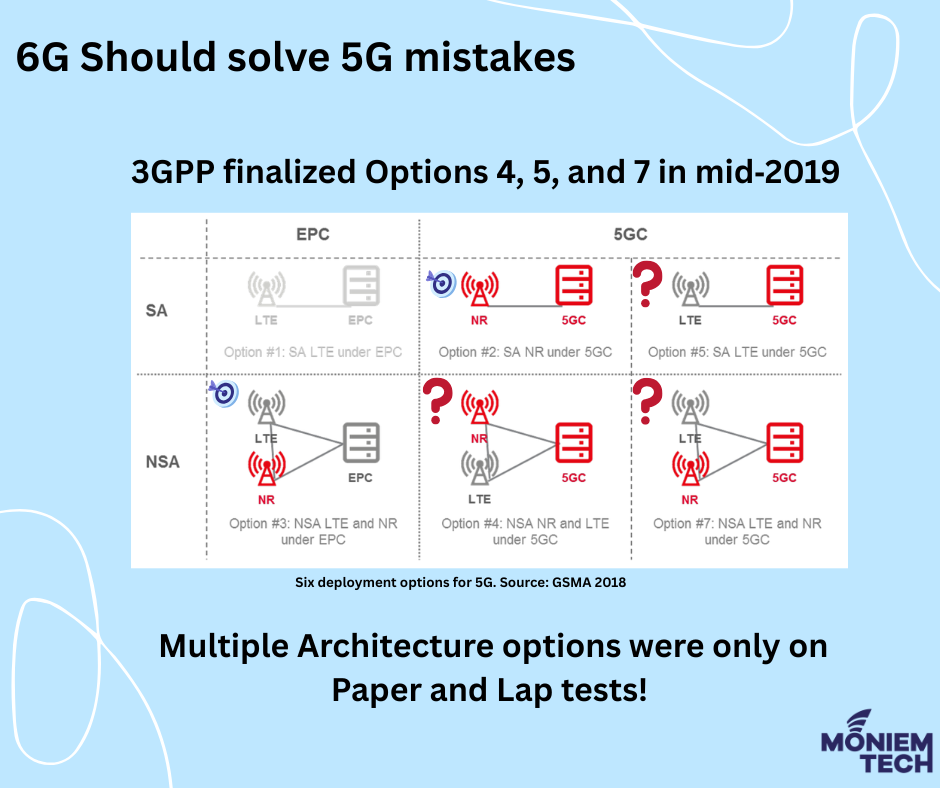
For the introduction of 5G, 3GPP has specified five possible configurations, or ‘options’, for connecting to an EPC or a new 5G core network (six if the current 4G system […]

Synchronization in 5G ensures precise timing and coordination across the network, enabling key technologies like TDD, beamforming, and ultra-low latency. 5G TDD networks utilise the same frequency for both uplink […]
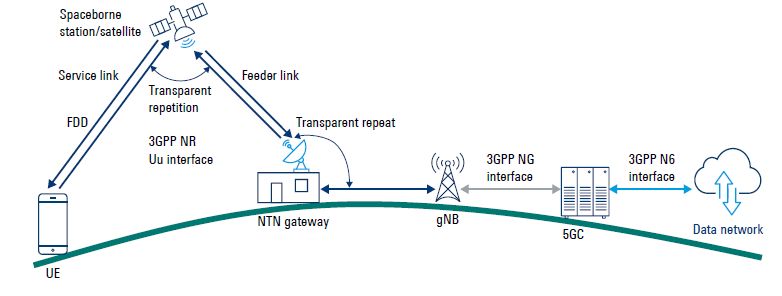
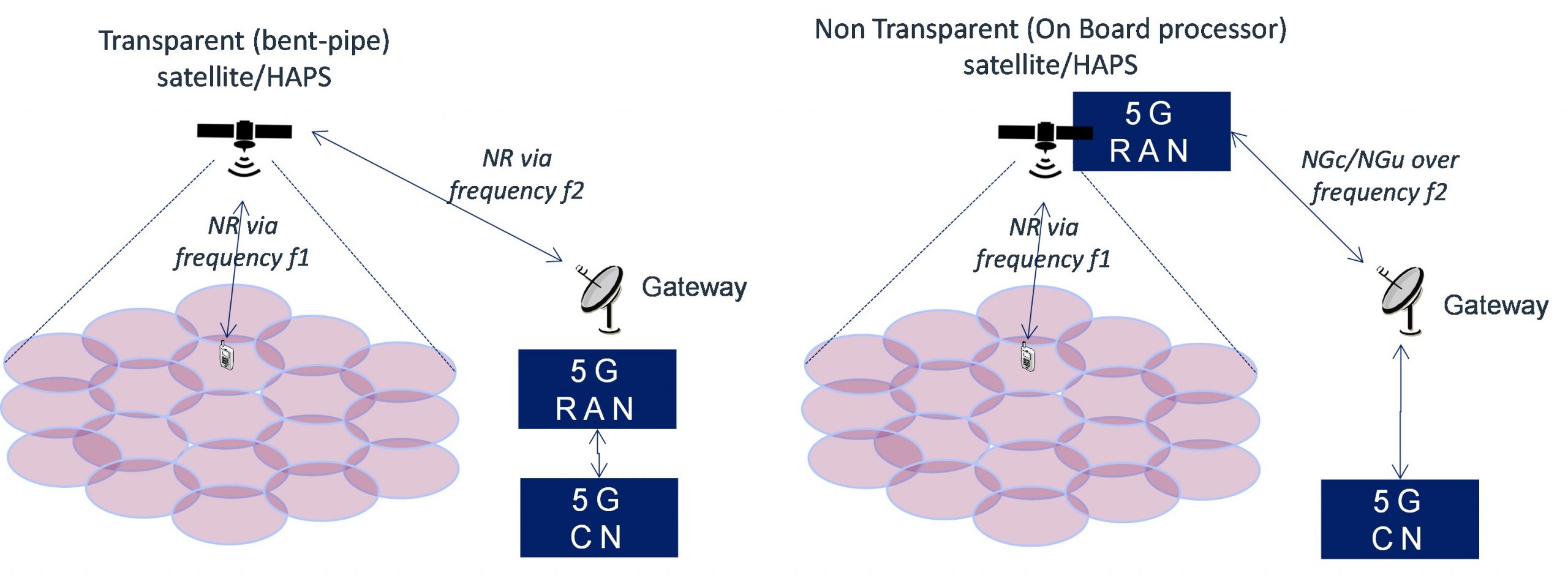
The 5G Non-Terrestrial Network (NTN) integrates satellite and airborne platforms with terrestrial 5G networks to provide ubiquitous coverage. The Next-Generation Radio Access Network (NG-RAN) architecture in 5G NTN can be designed to […]
