The journey started with 2G and 3G, where Voice was the leading service, and the main protocols were SS7 and SIGTRAN (Signaling Transport). At this time, the primary Firewalls are: […]
Before discussing why we need an SMS Router, let’s understand the 1st figure when the mobile device sends SMS to another Mobile through the normal scenario without an SMS Router […]
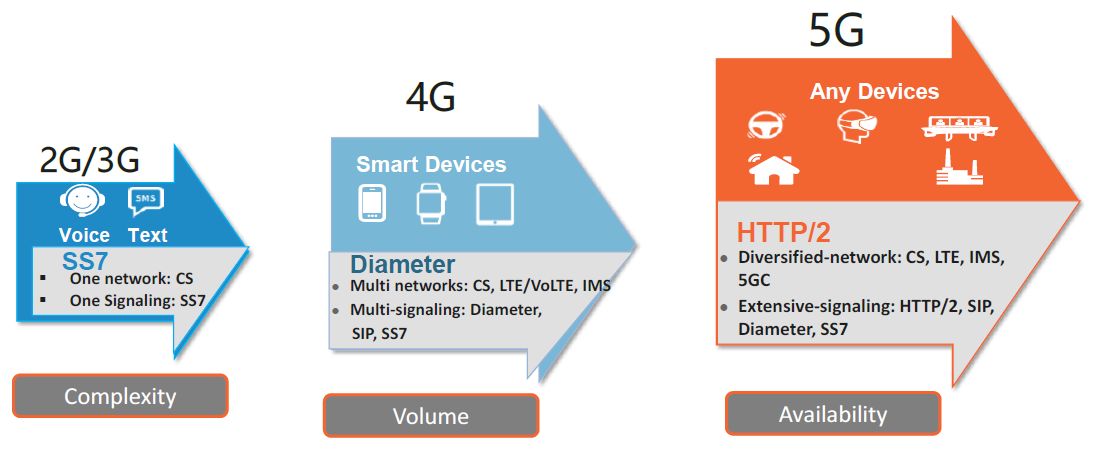
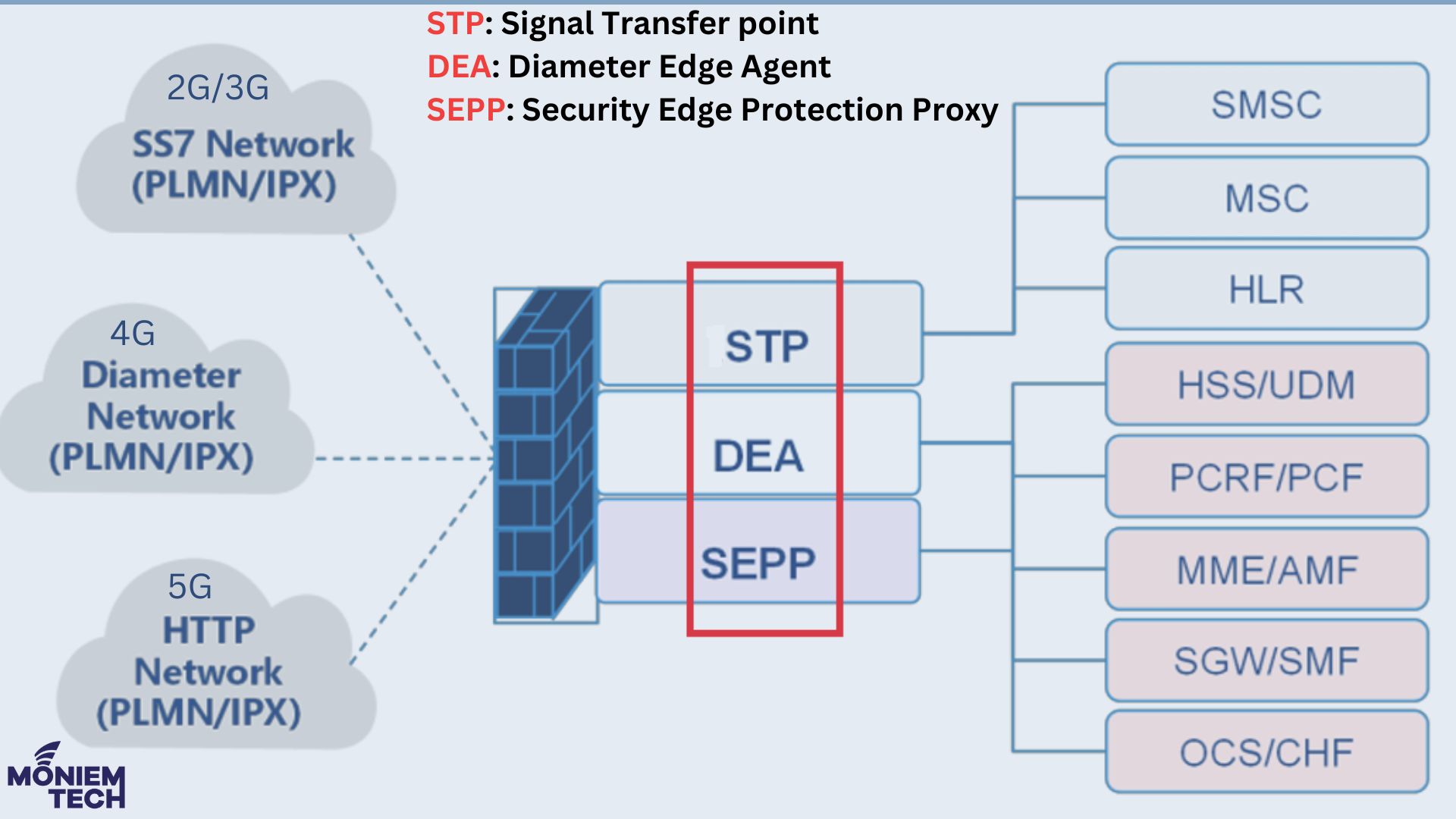
?In 2G and 3G, voice and text were the main services based on SS7 signaling. In these networks service availability was the priority. The Signal Transfer Point (STP) was the […]

Before starting to talk about IMSI Catcher, we need to understand what is the IMSI, its importance, and its structure. Based on this, we will discuss the IMSI catcher. So […]
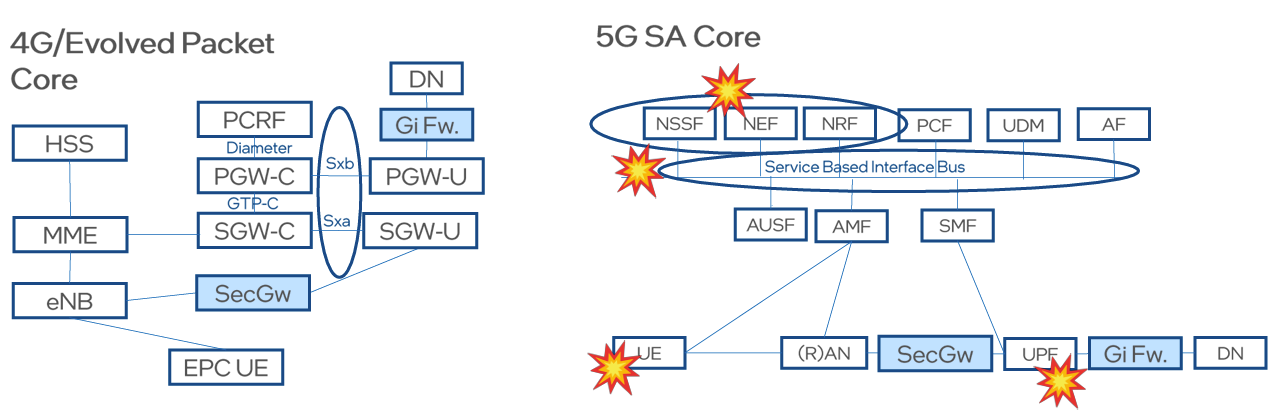
If you look at how security was addressed in the 4G core (EPC), you had perimeter devices, whether it’s firewalls, security devices that protect from denial of service attacks, or […]
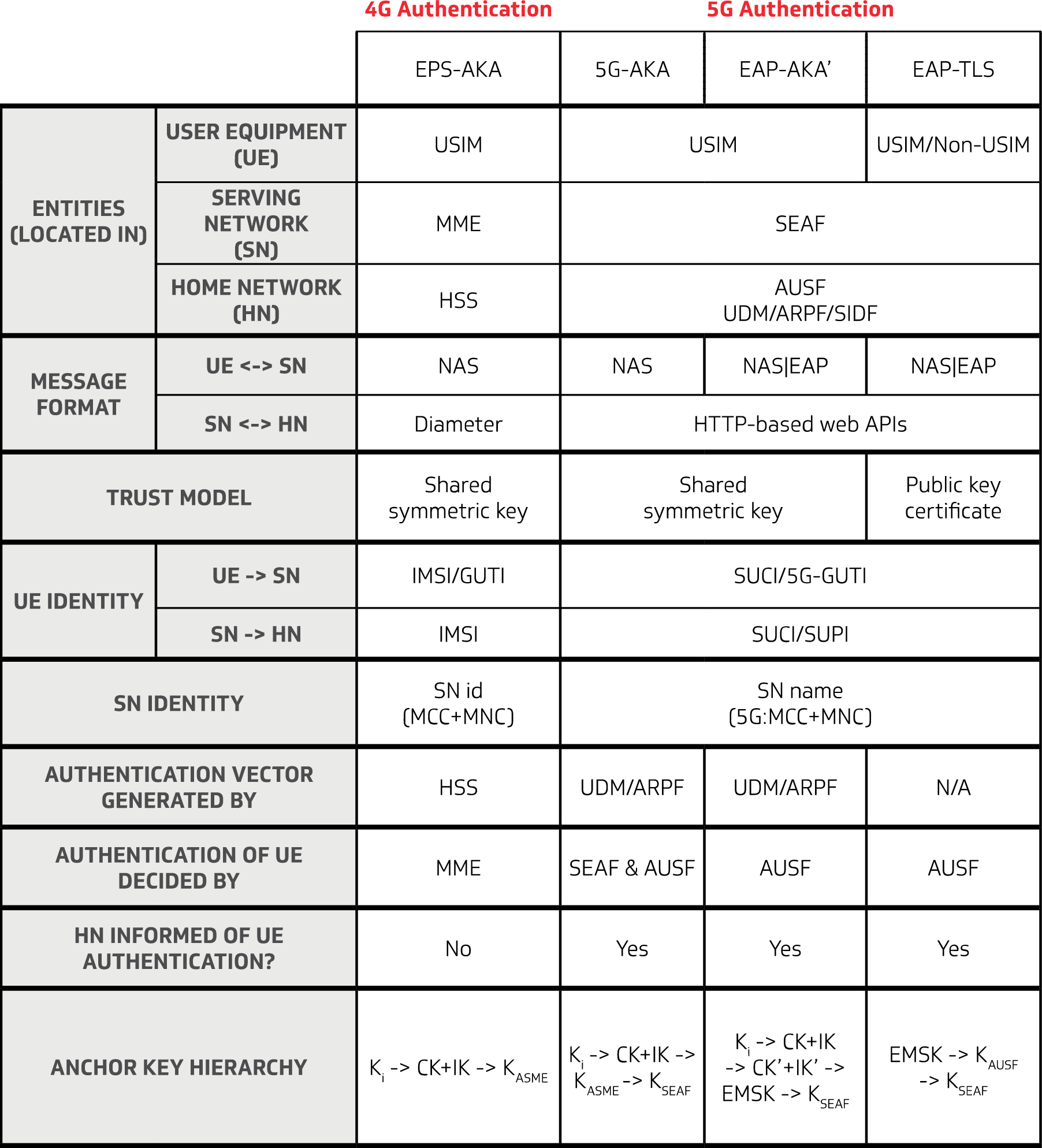
The authentication procedure in 3GPP 5G security has been designed as a framework to support the Extensible Authentication Protocol (EAP) – a security protocol specified by the Internet Engineering Task […]

5G Timeline and Standardization During preparation, it was decided to split Phase 1 into two parts. In December 2017, standardization of the non-autonomous, or Non-Standalone, architecture for 5G New Radio […]

Introduction 5G will give a diverse and new set of services and use cases affecting nearly every aspect of our lives. But to exceed all expectations, 5G-enabled services and applications […]
